Deep experience in the field of System Engineering, Architecting Middleware & BPM, Decision Management solutions. Experience in Software development includes analysis, design and development of web based applications & Multi-tier applications. Broad knowledge on application and system architecture and design capabilities over many technologies to im-plement secure, robust, transactional and service oriented architectures.
Monday, October 12, 2009
AIX 6.1 - Workload Partitions (WPARs)
Virtualization unquestionably saves a lot of money on power and cooling. The more partitions you can carve on your existing systems, the better utilization you will have. WPAR, a new innovation of AIX 6.1, allow for operating systems virtualization, outside of traditional hypervisor-based logical partitioning. In essence, it allows you to carve up multiple workload environments inside of one host and OS kernel. So you can now have one single instance of AIX 6.1 and using WPARs you can have four different test environments working within that instance, appearing like separate operating system instances. Prior to WPARs, you would need to carve out separate logical partitions (LPARs) within the physical server.
This new feature of AIX 6.1 has the effect of reducing the amount of physical devices necessary to support your logical environments. Though one can conceivably get by with the bare minimum of physical devices for a logical partition, the WPAR is clearly the most efficient means that you can use when creating a new environment. This is purely an AIX innovation, unrelated to the POWER6. Furthermore, Live Application Mobility, another AIX 6.1 innovation, allows you to relocate running WPARs from one LPAR to another. IBM is the first vendor that allows for this feature without having to shut down the application or partition. This helps promote energy savings by allowing datacenter operators to move around workloads in such a way as to allow physical servers to sleep during non-peak periods. This feature is available on Power5™ servers and even Power4™ as well!
Thursday, October 8, 2009
Human Resources organization is optimized
You are invited to participate in Bersin & Associates' major research study to help you answer these questions in detail: The High-Impact HR Organization. This research study is a comprehensive look at trends and best-practices in the organization, management, and operations of Human Resources.
Goals of this study:
HR executives and professionals need ways to deliver ever-greater levels of service, support, and talent management solutions to their organizations. Today's business climate - with its rapidly changing workforce, economic challenges, regulatory requirements, and evolving technologies – demands that HR re-evaluate its role, structure, and delivery strategy to drive employee and business value.
This in-depth research will look at best-practices in HR organization, structure, roles, technology, service-delivery, program strategy, and resource allocation. The goal is to provide you a proven set of modern solutions you can use to improve the impact of HR.
As a participant in this research, you will be able to contribute, learn, and benchmark your organization against these best practices. All research participants will receive a detailed overview of study findings and will be invited to a special webinar presenting the results
In appreciation for your time, you will also receive a copy of our recently published 2009 Career Factbook for HR and Learning Professionals. This 130 page report provides a comprehensive view of career paths, competencies, compensation, education, motivation, and the challenges of HR and L&D professionals.
Please click here to participate. This survey will take you approximately 20 minutes to complete. If you have any questions about this research, please contact Bersin & Associates at info@bersin.com. For more background on this research, please visit http://www.bersin.com/hihr.
Thank you for your participation.
Monday, July 13, 2009
Preparing to host applications.
Operating Systems: AIX, HP-UX, i5/OS, Linux, Solaris, Windows, z/OS
Preparing to host applications
Rather than use the default application server provided with the product, you can configure a new server and set of resources.
About this task
The default application server and a set of default resources are available to help you begin quickly. You can choose instead to configure a new server and set of resources. Here is what you need to do in order to set up a runtime environment to support applications.
Procedure
1. Configure an application server.
2. Create a virtual host.
3. Configure a Web container.
4. Configure an EJB container.
5. Create resources for data access.
6. Create a JDBC provider and data source.
7. Create a URL and URL provider.
8. Create a JavaMail session.
9. Create resources for session support.
10. Configure a Session Manager.
Sunday, June 14, 2009
WebSphere Message Broker V6.1 - Fix Pack 6.1.0.4
Abstract
This is Fix Pack 6.1.0.4 for WebSphere Message Broker Version 6.1
Download Description
Fix Pack 6.1.0.4 is the fourth maintenance for WebSphere Message Broker Version 6.1. It is available for the following platforms:
AIX
HP-UX
HP-UX Itanium
Linux
Linux on zSeries
Linux (Power)
Linux on Intel x86
Sun Solaris
Solaris x86-64
Windows 2003 and Windows XP
z/OS
Note that this Fix Pack is for the broker product only. Updates for the toolkit are available from the product Toolkit links on the following
URL : http://www-1.ibm.com/support/docview.wss?uid=swg27006041
Prerequisites
Install the Fix Pack on top of IBM WebSphere Message Broker Version 6.1.
The link below gives the supported environments for IBM WebSphere Message Broker V6.1 and it's components.
URL LANGUAGE SIZE(Bytes)
System Requirements English 9999
Installation Instructions
Instructions for applying maintenance are given in the product Infocenter, under the heading "Installing". You can view the Infocenter Online or via your Message Brokers Toolkit, or download the PDF file "Managing your Installation" from the Library link below.
These instructions must be amended by any changes documented in the latest product readme file and any changes documented in the Release Notes, below.
URL LANGUAGE SIZE(Bytes)
Problems Fixed English 9999
WebSphere Message Broker Library English 9999
Readme English 9999
Release Notes English 9999
Download package
What is Fix Central (FC)?
Download RELEASE DATE LANGUAGE SIZE(Bytes) Download Options
AIX 11/06/2009 Language Independent 471955609 FC
HP-UX 11/06/2009 Language Independent 502067148 FC
HP Itanium 11/06/2009 Language Independent 412594521 FC
Solaris SPARC 11/06/2009 Language Independent 377896150 FC
Solaris X86-64 11/06/2009 Language Independent 313041059 FC
Linux x86 11/06/2009 Language Independent 291632615 FC
Linux s390x (zSeries) 11/06/2009 Language Independent 286513941 FC
Linux PPC 11/06/2009 Language Independent 295896193 FC
Linux x86-64 11/06/2009 Language Independent 394557011 FC
Windows 11/06/2009 Language Independent 251496632 FC
z/OS 11/06/2009 Language Independent 203107328 FC
Problems (APARS) fixed
IC54662, IC54505, IC54555, PK57973, PK57974, PK57975, PK57976, PK54892, PK59269, IC56211, PK64389, PK64390, PK64391, PK64397, PK65847, IC53957, IC53997, IC54097, IC54202, IC54484, IC54524, IC54633, IC54698, IC54737, IC54749, IC54755, IC54784, IC54958, IC54963, IC54985, IC55034, IC55146, IC55254, IC55257, IC55271, IC55298, IC55311, IC55424, IC55507, IC55521, IC55578, IC55608, IC55613, IC55689, IC55997, IC56013, IC56113, IC56190, IC56236, IY89266, IY94881, IY97796, IZ02427, IZ02657, IZ04441, IZ05008, IZ06546, IZ06738, IZ06984, IZ07456, IZ08644, IZ08787, IZ09066, IZ10043, IZ12481, IZ13223, IZ13831, IZ13992, IZ14327, IZ14470, IZ15182, IZ15371, IZ15987, IZ16570, IZ17454, IZ17623, IZ19550, PK53829, PK55676, PK59124, PK59650, PK61664, PK63922, IC57836, PK71665, PK71666, PK71669, PK71705, IC54769, IC55028, IC55033, IC55502, IC55513, IC55514, IC55871, IC55987, IC56239, IC56296, IC56349, IC56457, IC56497, IC56525, IC56531, IC56566, IC56710, IC56790, IC56793, IC56802, IC56847, IC56853, IC56898, IC56912, IC56916, IC56918, IC57012, IC57021, IC57022, IC57057, IC57105, IC57159, IC57319, IC57327, IC57335, IC57375, IC57451, IC57469, IC57476, IC57534, IC57572, IC57573, IC57587, IC57599, IC57602, IC57689, IC57705, IC57834, IC57886, IC57946, IC58134, IC58202, IC58205, IC58260, IC58261, IC58286, IC58542, IC58785, IC59016, IZ15874, IZ18000, IZ18492, IZ18912, IZ20361, IZ20680, IZ20708, IZ21068, IZ22174, IZ22782, IZ22999, IZ23135, IZ23315, IZ25616, IZ26492, IZ27860, IZ27873, IZ33255, PK63949, PK67146, PK69088, PK70138, PK70374, PK72103, PK73298, IC54781, IC55513, IC57088, IC57219, IC57560, IC57650, IC58217, IC58247, IC58363, IC58455, IC58467, IC58607, IC58621, IC58716, IC58786, IC58866, IC58890, IC58935, IC58943, IC58946, IC58951, IC58961, IC59034, IC59051, IC59058, IC59090, IC59107, IC59116, IC59128, IC59142, IC59164, IC59190, IC59197, IC59201, IC59217, IC59229, IC59250, IC59260, IC59303, IC59320, IC59398, IC59402, IC59417, IC59467, IC59618, IC59641, IC59642, IC59644, IC59672, IC59673, IC59717, IC59818, IC59851, IC59897, IC59899, IC59900, IC59901, IC59933, IC60078, IC60103, IC60118, IC60152, IC60154, IC60237, IC60238, IC60247, IC60311, IC60316, IC60332, IC60333, IC60394, IC60397, IC60401, IC60428, IC60449, IC60454, IC60916, IZ22756, IZ28848, IZ30043, IZ31895, IZ32333, IZ33918, IZ34287, IZ35449, IZ35623, IZ35853, IZ36932, IZ37666, IZ38636, IZ38978, IZ39246, IZ39312, IZ39419, IZ40853, IZ40999, IZ41957, IZ42616, IZ42696, IZ43211, IZ43892, IZ44450, IZ44920, IZ46862, PK72883, PK73212, PK74382, PK74968, PK76235, PK77862, PK81096, PK81355, PK81837, PK81907, PK81924, PK82423, PK82443, PK82545, PK83041, PK83232, PK84635, PK85152
Copyright and trademark information
IBM, the IBM logo and ibm.com are trademarks of International Business Machines Corp., registered in many jurisdictions worldwide. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on the Web at "Copyright and trademark information" at www.ibm.com/legal/copytrade.shtml.
Saturday, June 13, 2009
Get group discounts at IBM's Rational Software Conference 2009
|
Tuesday, May 26, 2009
Writitng Verbose GC to a Specified Log –Xverbosegclog, How do you get verbose GC output to another log besides native_stderr?
WebSphere Application Server 7.0
-Xverbosegclog[:
Causes -verbose:gc output to be written to the specified file. If the file cannot be found, -verbose:gc tries to create the file, and then continues as normal if it is successful. If it cannot create the file (for example, if an invalid filename is passed into the command), it will redirect the output to stderr.
If you specify
The dump agent tokens can be used in the filename. See Dump agent tokens for more information. If you do not specify
Dump agent tokens
Use tokens to add context to dump file names and to pass command-line arguments to the tool agent.
The tokens available are listed in the table below:
Token Description
%Y Year (4 digits)
%y Year (2 digits)
%m Month (2 digits)
%d Day of the month (2 digits)
%H Hour (2 digits)
%M Minute (2 digits)
%S Second (2 digits)
%pid Process id
%uid User name
%seq Dump counter
%tick msec counter
%home Java™ home directory
%last Last dump
%job Job name (z/OS® only)
&DS Dump Section.
An incrementing sequence number used for splitting TDUMP files to be less than 2 GB in size. (z/OS 64-bit version 1.10 or newer only)
1. In the administrative console, click Servers > Server Types > WebSphere application servers > server_name. Then, under Server Infrastructure, click Java™ and process management > Process definition.
2. Select Java Virtual Machine .
3. Specify values for the JVM settings as needed and click OK.
4. Click Save on the console task bar.
5. Restart the application server.
WebSphere Application Server 6.1
-Xverbosegclog:
Causes -verbose:gc output to be written to the specified file. If the file cannot be found, -verbose:gc tries to create the file, and then continues as normal if it is successful. If it cannot create the file (for example, if an invalid filename is passed into the command), it will redirect the output to stderr.
If you specify
1. In the administrative console, click Servers > Application Servers >server. Then, under Server Infrastructure, click > Java and Process Management > Process Definition .
2. Select Java Virtual Machine.
3. Specify values for the JVM settings as needed and click OK.
4. Click Save on the console task bar.
5. Restart the application server.
WebSphere Application Server 6.0 and 5.1
-Xverbosegclog:
Causes verboseGC output to be written to the specified file. If the file cannot be found, verboseGC tries to create the file, and then continues as normal if it is successful. If it cannot create the file (for example, if an invalid filename is passed into the command), it will redirect the output to stderr. Use .%p to append the process id to the file name.
-Xverbosegclog:
1. Filename must contain a "#" (hash symbol), which is substituted with a generation identifier, starting at X and Y are integers. This option works similarly to -Xverbosegclog:
**Example: -Xverbosegclog:/opt/WebSphere/logs/gc#.log,50,100
The above setting would create 50 log files named gc
2. In the administrative console, click Servers > Application Servers >server. Then, under Server Infrastructure, click > Java and Process Management > Process Definition .
3. Select Java Virtual Machine.
4. Specify values for the JVM settings as needed and click OK.
5. Click Save on the console task bar.
6. Restart the application server.
Monday, April 6, 2009
What is Secure Sockets Layer (SSL) Overview
Privacy and security are concepts that are more critical than ever in today’s electronic business
environment.
Every business professional needs to be concerned about security over open communication
networks, such as the Internet. It is not enough to have a secure Web site; you also need to have
secure communication between Web sites, communication that cannot be monitored by outside
parties. Both you and your users need to be confident that you have a secure environment in
which to conduct your business.
That kind of secure communication requires encryption, and encryption is what the Secure
Sockets Layer (SSL) provides: security for the connection over which you can communicate.
SSL was developed jointly by Netscape Communications and RSA Data Security. Many
companies worldwide have adopted SSL as their communication protocol of choice. In fact,
many financial transactions on the Internet, including online banking, are now conducted using
SSL.
Because digital certificates are an important component of SSL.
What is Digital certificate
Digital certificates allow unique identification of an entity; they are, in essence, electronic ID
cards issued by trusted parties. Digital certificates allow a user to verify to whom a certificate is
issued as well as the issuer of the certificate.
Digital certificates are the vehicle that SSL uses for public-key cryptography. Public-key
cryptography uses two different cryptographic keys: a private key and a public key. Public-key
cryptography is also known as asymmetric cryptography, because you can encrypt information
with one key and decrypt it with the complement key from a given public-private key pair.
Public-private key pairs are simply long strings of data that act as keys to a user's encryption
scheme. The user keeps the private key in a secure place (for example, encrypted on a computer's
hard drive) and provides the public key to anyone with whom the user wants to communicate.
The private key is used to digitally sign all secure communications sent from the user; the public
key is used by the recipient to verify the sender's signature.
Public-key cryptography is built on trust; the recipient of a public key needs to have confidence
that the key really belongs to the sender and not to an impostor. Digital certificates provide that
confidence.
A digital certificate serves two purposes: it establishes the owner’s identity, and it makes the
owner's public key available. A digital certificate is issued by a trusted authority—a certificate
authority (CA)—and it is issued only for a limited time. When its expiration date passes, the
digital certificate must be replaced.
Format of digital certificates
The digital certificate contains specific pieces of information about the identity of the certificate
owner and about the certificate authority:
_ Owner's distinguished name. A distinguished name is the combination of the owner's
common name and its context (position) in the directory tree. In the simple directory tree
shown in Figure 1, for example, LaurenA is the owner's common name, and the context
is OU=Engnring.O=XYZCorp; therefore, the distinguished name is:
.CN=LaurenA.OU=Engnring.O=XYZCorp

_ Owner's public key.
_ Date the digital certificate was issued.
_ Date the digital certificate expires.
_ Issuer's distinguished name. This is the distinguished name of the CA.
_ Issuer's digital signature.
What is CA SiteMinder®Web Access Manager
SECURITY MANAGEMENT FOUNDATION THAT ENABLES THE SECURE USE OF THE WEB TO DELIVER
APPLICATIONS AND DATA TO CUSTOMERS, PARTNERS AND EMPLOYEES.
Overview
Your customers, partners and employees fully expect anytime, anywhere access to your critical applications, information and services. The proliferation of intranets, B2B extranets and e-commerce
Websites presents opportunities to increase revenues, manage costs and deepen relationships with users. But opening your organization via the Web also presents significant security, management and compliance challenges.
Benefits
CA SiteMinder WAM lets you manage and deploy secure web applications to:
• Increase new business opportunities
• Manage costs
• Improve security to mitigate risk
• Ease compliance
The CA Advantage
CA SiteMinder WAM delivers unparalleled reliability, availability, scalability and manageability.
The de facto gold standard for enterprise-class web access management, CA SiteMinder WAM is also a key part of the CA Identity & Access Management (CA IAM) solution, which automates the administration of user identities and ensures only properly authorized users can access critical IT resources from the Web to the mainframe. This in turn is part of CA’s vision for Enterprise IT Management (EITM).
CA SiteMinder WAM Centralizes Web Access Management and Security Policy
For all the promise of the Web to increase revenues, manage costs and deepen relationships
with users, it also raises a new class of security, management and compliance challenges. As
your IT organization deploys applications with web front-ends and looks to build and manage
websites and portals to meet the information and access needs of potentially millions of users
both inside and outside your enterprise, a fundamental question looms: How do you let business
in while keeping risk out?
The answer is CA SiteMinder Web Access Manager. With advanced security management
capabilities and enterprise-class site administration, CA SiteMinder WAM provides the centralized
security management your organization needs to authenticate users and control access to web
applications and portals. Across Internet and intranet applications, it enables the secure delivery
of essential information and applications to your employees, partners, suppliers and customers.
It also scales to meet your growing business needs with flexible administration tools that can
support either centralized or distributed administration.
Use CA SiteMinder WAM to build and manage secure websites that offer a rich user experience,
simplified administration, enterprise-class security and 24 × 7 availability.
Key Capabilities
SINGLE SIGN-ON (SSO) CA SiteMinder WAM eliminates the challenge of multiple user logins
by enabling single sign-on for seamless access across multiple diverse web applications,
portals and security domains. Seamless access to enterprise applications such as SAP, Siebel,
PeopleSoft and Oracle is also supported through the SSO capability of CA SiteMinder WAM.
Integration with CA Single-Sign-On (CA SSO), the enterprise SSO component of the CA Identity &
Access Management solution, enables users to authenticate only once and have access both to
web applications protected by CA SiteMinder WAM and non-web applications with access
controlled by CA SSO.
STRONG AUTHENTICATION MANAGEMENT CA SiteMinder WAM provides a unified authentication
strategy to ensure the right level of security across Internet and intranet applications. This
ensures that high value applications are protected by stronger authentication methods while
lower value applications may be protected by simpler user name/password approaches.
CA SiteMinder WAM provides access management support for many authentication systems —
including passwords, tokens, X.509 certificates, smartcards, custom forms, biometrics — and
combinations of authentication methods.
In addition, CA SiteMinder WAM enables authorization policies to incorporate authentication
context. For example, when two authentication methods are in use by a particular organization
(for example username/password and one-time password tokens) and the user authenticates
with the one-time password, the user can be granted increased application entitlements.
CENTRALIZED, POLICY-BASED AUTHORIZATION, AUDIT, AND REPORTING CA SiteMinder
WAM centralizes the access management for customers, partners and employees across an
enterprise’s web applications. This eliminates the need for redundant, application-specific
security logic and provides a lower cost approach for ensuring an enterprise’s ability to meet
compliance requirements. CA SiteMinder WAM policies are rules or rule groups that allow
or deny access to a resource. Access can be restricted by user attributes, roles, groups and
dynamic groups and determined based on location and time. Authorization can be conducted
at the file, page or object level. In addition, controlled “impersonation” — where one
authorized user, such as a customer service representative, can access what another user
can access — is also defined by policies. An embedded policy analysis engine, reporting
system, and out of the box reports support an organization’s evolving needs for compliance
and governance reporting.
Dynamic Authorization triggers security policies that evaluate data in real time from a variety
of local or external sources, including Web services and databases, to determine access
authorization or denial. Finer-grained authorization is achieved through contextual evaluation.
For example, limit access to a specific application (a certain banking service) to customers who
meet specific criteria (a minimum account balance). Authorization policies can also be applied
in conjunction with external systems, such as risk-based security systems.
ENTERPRISE MANAGEABILITY CA SiteMinder WAM provides enterprise-class system management
tools, which gives security personnel the ability to monitor, manage and maintain multiple
environments more efficiently, including the management of development, test and production
environments. These management tools include:
• Unattended installs
• Operational monitoring
• Rolling upgrades
• Centralized web agent management
• Application management abstraction
• Delegated and segregated management
• Web-based administrative UI
• Security policy migration
• Security zones
• Scripting interface capabilities
SCALABILITY AND RELIABILITY CA SiteMinder WAM can be scaled to meet enterprise-class
security requirements both in terms of the number of users and number of protected resources,
ensuring its ability to handle growth, including growth from acquisitions or partnerships.
Use CA SiteMinder WAM to deploy critical business applications to multimillion user populations
and be confident that its performance has been verified through independent testing to provide
significantly higher transaction rates, reliability and manageability than alternative solutions.
Reliability, availability and scalability are supported by features including:
• Dynamic load balancing
• Two-level caching
• Policy Server clustering and cluster-to-cluster failover
• Policy Store and user store replication
• Support for 4- and 8-way SMP servers
IDENTITY FEDERATION CA SiteMinder WAM also provides an architecturally integrated,
separately-licensed capability that enables browser-based federation whereby users can securely
traverse from home sites (identity provider) to websites hosted by partners and customers (service
provider). CA SiteMinder WAM customers can play the role of either website in a federation.
The federation functionality, called CA Federation Manager, provides a flexible and robust
platform for identity federation, enabling organizations to realize the benefits of connecting
distributed business applications across domains without sacrificing security. CA Federation
Manager supports a comprehensive set of federation standards, including the Security
Assertion Markup Language (SAML) and WS-Federation/Microsoft ADFS. It enables complete,
bidirectional federation from a single Web security system with maximum interoperability
among partnering enterprises. In addition CA SiteMinder WAM can be extended to provide
security for Web services through the addition of CA SOA Security Manager.
HOW CA SITEMINDER WEB ACCESS MANAGER WORKS

The process for securely accessing
web applications:
1 User attempts to access a protected
resource.
2 User is challenged for credentials and
presents them to the CA SiteMinder
web agent or to the Secure Proxy
Server.
3 The user’s credentials are passed to
the Policy Server.
4 The user is authenticated against the
appropriate user store.
5 The Policy Server evaluates the user’s
entitlements and grants access.
6 User profile and entitlement information
is passed to the application.
7 The user gets access to the secured
application, which delivers customized content.
CA SiteMinder WAM Supports Online Business, Enhances User
Satisfaction, Mitigates Costs and Increases IT Control and Security
The Web is open for business around-the-clock, and CA SiteMinder WAM reliably and
effectively enables your online presence to be secure, available and accessible to the right
users. Recognized for having the most advanced security management capabilities and
enterprise-class site administration, CA SiteMinder WAM can scale to support millions of
users and thousands of protected resources.
CA SiteMinder WAM allows you to meet the challenge of deploying resources via the Web
while maintaining high performance and high availability. It controls who is able to access
which applications and under what conditions, improves users’ online experiences and
simplifies security administration. By enforcing policies and monitoring and reporting online
activities and user privileges, CA SiteMinder WAM also eases regulatory compliance.
ENSURE THE RIGHT USERS HAVE THE RIGHT ACCESS With CA SiteMinder WAM, the secure
management of identities across diverse web systems means the system controls access by
leveraging the user’s context to the business (partner, consultant, customer, etc.) and their
rights to each application. CA SiteMinder WAM enables users to connect to the information
and applications they need to do their jobs, place an order or otherwise transact business.
INCREASE SECURITY TO MITIGATE RISKS CA SiteMinder WAM reduces the risk of unauthorized
access to critical resources and sensitive information, protecting the content of an entire web
portal or set of applications. Centralized security enforcement and FIPS certified cryptographic
algorithms means that there are no holes left open in a CA SiteMinder WAM secured web
environment.
PROVIDE USERS WITH A POSITIVE ONLINE EXPERIENCE CA SiteMinder WAM lets a user sign on
once to access web applications, engaging them in a unified, personalized online experience
rather than frustrating them with multiple logins.
INCREASE BUSINESS OPPORTUNITIES CA SiteMinder WAM lets you securely deploy web
applications to multiple different user communities, enabling increased business opportunities
that can enhance revenue. Extend CA SiteMinder WAM with identity federation and your
organization can improve collaboration with partners, further enhancing relationships to
increase revenue, manage cost and mitigate risk
MANAGE COSTS CA SiteMinder WAM mitigates IT administration costs. It also reduces the
security burden on users and thus the burden on the help desk caused by lost or forgotten
credentials. It also reduces redundant security-related application development and
maintenance costs.
EASE REGULATORY COMPLIANCE Central policy management, enforcement, reporting and
auditing support your ability to comply with IT impacting regulations.

The CA Advantage
CA SiteMinder WAM is part of the complete and proven CA IAM solution that helps you protect
your IT assets across all platforms and environments. As such, it contributes to your ability to
optimize the performance, reliability and efficiency of your overall IT environment. The next step
is to tightly integrate the control and management of distinct functions such as operations, storage
and life cycle and service management, along with IT security.
This higher level of management control is CA’s vision for EITM — a dynamic and secure approach
that integrates and automates the management of applications, databases, networks, security,
storage and systems across departments and disciplines to maximize the full potential of each.
CA’s comprehensive portfolio of modular IT management solutions helps the enterprise unify,
simplify and secure IT to better manage risk, costs and service, and ensure that IT meets the
business needs of the enterprise.
Next Steps
To fully leverage the reach and power of the Web, investigate the breadth and depth of
CA SiteMinder Web Access Manager. As the most comprehensive, scalable and reliable
Web Access Management solution on the market, it supports your organization’s ability to
increase new business opportunities, manage costs, improve security to mitigate risk and
ease compliance.
Friday, March 27, 2009
Unix, Linux administration interview questions
LILO stands for Linux boot loader. It will load the MBR, master boot record, into the memory, and tell the system which partition and hard drive to boot from.
What is the main advantage of creating links to a file instead of copies of the file?
The main advantage is not really that it saves disk space (though it does that too) but, rather, that a change of permissions on the file is applied to all the link access points. The link will show permissions of lrwxrwxrwx but that is for the link itself and not the access to the file to which the link points. Thus if you want to change the permissions for a command, such as su, you only have to do it on the original. With copies you have to find all of the copies and change permission on each of the copies.
Write a command to find all of the files which have been accessed within the last 30 days.
find / -type f -atime -30 > December.files
This command will find all the files under root, which is ‘/’, with file type is file. ‘-atime -30′ will give all the files accessed less than 30 days ago. And the output will put into a file call December.files.
What is the most graceful way to get to run level single user mode?
The most graceful way is to use the command init s.
If you want to shut everything down before going to single user mode then do init 0 first and from the ok prompt do a boot -s.
What does the following command line produce? Explain each aspect of this line.
$ (date ; ps -ef | awk ‘{print $1}’ | sort | uniq | wc -l ) >> Activity.log
First let’s dissect the line: The date gives the date and time as the first command of the line, this is followed by the a list of all running processes in long form with UIDs listed first, this is the ps -ef. These are fed into the awk which filters out all but the UIDs; these UIDs are piped into sort for no discernible reason and then onto uniq (now we see the reason for the sort - uniq only works on sorted data - if the list is A, B, A, then A, B, A will be the output of uniq, but if it’s A, A, B then A, B is the output) which produces only one copy of each UID.
These UIDs are fed into wc -l which counts the lines - in this case the number of distinct UIDs running processes on the system. Finally the results of these two commands, the date and the wc -l, are appended to the file "Activity.log". Now to answer the question as to what this command line produces. This writes the date and time into the file Activity.log together with the number of distinct users who have processes running on the system at that time. If the file already exists, then these items are appended to the file, otherwise the file is created.
Thursday, March 26, 2009
IKEYCMD ( IKEYMAN ) Command Line Interface (gsk7cmd)
To run IKEYMAN , set up environment variables to use the IKEYCMD command line interface
as follows:
1. Set your PATH to where your Java or JRE executable resides:
EXPORT PATH=/opt/IBMJava/bin:$PATH
2. Set the following CLASSPATH environment variable:
EXPORT CLASSPATH=/usr/local/ibm/gsk/classes/cfwk.zip:/usr/local/ibm/gsk/classes/gsk4cls.jar:$CLASSPATH
Once completed, IKEYCMD should run from any directory. To run an IKEYCMD command,
use the following syntax:
java com.ibm.gsk.ikeyman.ikeycmd (command)
You can substitute JRE for Java, depending on whether you are using a JRE or JDK.
Example:
jre com.ibm.gsk.ikeyman.ikeycmd (command)
IKEYCMD Command Line Syntax
The syntax of the Java CLI is: java [-Dikeycmd.properties=
where:
-Dikeycmd.properties Specifies the name of an optional properties file to use for this Java
invocation. A default properties file, ikeycmd.properties, is provided as a sample file that can be modified and used by any Java application.
Object is one of the following:
-keydb Actions taken on the key database (either a CMS key database file, a WebDB keyring file, or SSLight class)
-cert Actions taken on a certificate
-certreq Actions taken on a certificate request
-help Display help for the IKEYCMD invocations
-version Display version information for IKEYCMD
Action is the specific action to be taken on the object, and options are the options, both required
and optional, specified for the object and action pair.
Note: The object and action keywords are positional and must be specified in the selected
order. However, options are not positional and can be specified in any order, provided
that they are specified as an option and operand pair.
User Interface Task Reference
IKEYCMD command line interface tasks are summarized in the following table.
IKEYMAN and IKEYCMD task
Create a new key database and specify the
database password
Create a new key pair and certificate request
Create a self-signed certificate
Export a key to another database or PKCS12 file
Import a key from another database or PKCS12
file
List certificate authorities (CAs) and certificate
requests
Open a key database
Receive a CA-signed certificate into a key
database
Show the default key in a key database
Store the root certificate of a CA
Store the encrypted database password in a stash
file
Friday, March 20, 2009
Free Trial - IBM WebSphere Message Broker, WebSphere Message Broker V6.1
Provides a smart approach to SOA, extending the reach of your business beyond your firewall by supporting a broad range of multiple transport protocols and data formats
Integrates multiple applications, networks, and device types using a platform-independent based enterprise service bus that lets you conduct business reliably and securely
Increases business agility and flexibility, extending easily to a Federated ESB model, while reducing development costs by separating integration logic from applications
Improves the flow of information around the business, moving away from hard-coded point-to-point links to more flexible distribution mechanisms such as publish/subscribe and multi-cast
Uses a simple programming model for connectivity and mediation, including a robust set of pre-built mediation function and ways to customize mediations
Exploits the industry-leading WebSphere MQ messaging infrastructure, and supports transformation options with graphical mapping, Java, ESQL, XSL, and WebSphere Transformation Extender
Delivers extensive administration and systems management facilities for developed solutions
Features and benefits of WebSphere Message Broker
IBM WebSphere® Message Broker V6.1 supports the following key capabilities and benefits:
Platform-Independent Based Enterprise Service Bus
Distribute any type of information across and between multiple diverse systems and applications, providing delivery of the right information in the right format at the right time
Reduce point-to-point interconnections and simplify application programming through separation of integration logic from the applications and from process logic
Powerful publish-and-subscribe matching engine routes information in real time based on topic and content to any endpoint
Validate and transform messages in-flight between any combination of different message formats, including Web Services, other XML and non-XML formats
Route messages based on (evaluated) business rules to match information content and business processes
Improve business agility by dynamically reconfiguring information distribution patterns without reprogramming end-point applications
Powerful runtime security model to address security concerns.
Integrated JCA based WebSphere Adapters as built-in nodes
Strengthens security and accelerates Web Services Security processing with DataPower SOA Appliance
Integration and enhancement of WebSphere Service Registry and Repository support to virtualize services for greater reuse
Enhance SOA support with advanced Web Services
Mediates (provides routing, transformation and logging) between Web Service requesters and providers
Mediates between Web Services and other integration models as both a service requester and a service provider
Delivers support for Web Services Security and Web Services Addressing, and compliance for Basic Profile
Works with the latest implementations of standards such as WSDL (Web Services Definition Language), SOAP (Simple Object Access Protocol), SOAP with attachments, any JMS (Java™ Message Service) HTTP(s) (Hypertext Transport Protocol), MTOM/XOP, and MQ
Enhanced support for provider and consumer scenarios
Toolkit support for WSDL drag and drop for skeleton flow creation and configuration
Full message set round-tripping for WSDL imports and exports.
New Web services parser creates more consumable message tree.
Integration without bounds with connectivity and transformation capabilities
Integrated WebSphere MQ transports - for Enterprise, Mobile, Real-Time, Multicast and Telemetry end points - extend the reach, scope and scale of the enterprise integration bus, out to mobile and handheld devices, along with embedded devices such as sensors or actuators.
Enable the secure and seamless interaction of enterprise applications with thousands of users within the Intranet and across the Internet
Provide native JMS interoperability, acting as a bridge between any combinations of different JMS providers.
Out-of-the-box nodes to simplify management and improve performance for key enterprise resource planning (ERP) integration scenarios (for example, SAP, Siebel, and PeopleSoft) through WebSphere Adapters packaged as native message-processing nodes
Native support for large file processing, including FTP, to simplify processing of large, repeating complex file records without using excessive storage
New Email Output node
Integration with WebSphere Transformation Extender, including the launcher, enabling WebSphere Transformation Extended maps to run natively in WebSphere Message Broker
Improved Consumability, Productivity and Systems Management
Provides a quick start with a single-click installation; install the product and run a sample in less than an hour
Simple packaging allowing for easy identification of appropriate install assets
Single install DVD for Windows and Linux desktops
ISMP installer for all platforms, SMP/.E for z/Os systems
Comprehensive "samples gallery" for all new and existing functions
Enterprise-wide identity, authentication, and authorization with Tivoli and Lightweight Directory Access Protocol (LDAP) servers to enforce service policy at the user level for greater security
Administration of both WebSphere MQ and WebSphere Message Broker networks in one console with the Eclipse-based Message Broker Explorer
Roll back with a single click
Extend your infrastructure with broader platform support and performance
Extend an existing WebSphere MQ and WebSphere Event Broker infrastructure
Available on IBM z/OS®, IBM AIX®, Linux (zSeries®, Intel, Power), Solaris (x86-64 and SPARC), HP/UX(PA-RISC, Itanium) and Microsoft® Windows® Server
Full range of industry standard databases includting support for DB2, SQL Server, Oracle, Sybase and Informix
Accounting and statistics reports support usage based charges and real-time graphical performance analysis for internal business charging
Enhanced SAP IDOC support
Improved binary data modeling within text messages.
64-bit capability on Linux and UNIX, Java Database Connectivity (JDBC) XA support, and Java 5 on all platforms
Ultra High Performance XML parser, including schema validation
Compacted memory footprint
Enhanced Developer Productivity
Eclipse based Message Broker Toolkit compatible with Rational Application Developer V6 and available on Windows and Linux
Data transformation options to match the data format and the developer skill set
Reduced toolkit size with enhanced look and feel improvements including productivity aids.
Standards based metadata including XML Schema and Web Services Definition Language
Java Debug Protocol (JDP) enabled withing toolkit
Graphical message metadata and mapping definition
Visual trace capability to display message path through flow in real time in Eclipse
New message viewer to graphically identify source and/or target message element locations
Simplified development with a configuration-drive approach for all new nodes
Eclipse based Type Designer and Map Designer integrated with the toolkit
Download a free trial version of WebSphere Message Broker V6.1
Sunday, March 8, 2009
History of IBM Websphere Application Server (WAS), What is WAS.
a software application server, is the flagship product within IBM's Websphere brand. WAS is built using open standards such as Java EE, XML, and Web Services. It works with a number of Web servers including Apache HTTP Server, Netscape Enterprise Server, Microsoft Internet Information Services (IIS), IBM HTTP Server for i5/OS, IBM HTTP Server for z/OS, and IBM HTTP Server for AIX/Linux/Microsoft Windows/Solaris.
WAS Versions
Version 1 of IBM WebSphere Application Server (WAS).
IBM has shipped several versions and editions of WAS. In the first beta versions, WAS was called Servlet Express.
What started it all in June, 1998. Really only a Java Servlet engine at that point.
Version 2 of IBM WebSphere Application Server (WAS).
In this version IBM adds JavaBean and CORBA support. Now supports Linux. Comes in two editions: Standard Edition (SE) and Advanced Edition (AE).
Version 3 of IBM WebSphere Application Server (WAS).
This version of WAS was compatible with a JDK 1.2, J2EE 1.0 version. IBM provided many enhancements to the basic J2EE 1.0 spec. Support for OS/400 (now i5/OS) and OS/390 (now z/OS) was added, although the z/OS version maintained a substantially separate codebase until v5.x. Version 3 is distributed in three editions: Standard Edition (SE), Advanced Edition (AE), and Enterprise Edition (EE).
Version 3.5 of IBM WebSphere Application Server (WAS).
This version was shipped in following editions:
· SE (Standard Edition)
· AE (Advanced Edition)
· EE (Enterprise Edition)
Version 4 of IBM WebSphere Application Server (WAS).
This was a J2EE 1.2 certified application server. It inherited the database-based configuration model from V3.x for all but the single-server edition, which already used an XML datastore.
· AE (Advanced Edition)
· AEs (Advanced Edition single). Single-server edition that was not able to run in a cluster configuration.
· AEd (Developer Edition). Functionally equivalent to AEs, but intended only for non-production development use.
· EE (Enterprise Edition)
Version 5 of IBM WebSphere Application Server (WAS).
The version released on 19 November 2002. This was a J2EE 1.3 certified application server. It was a major rewrite of the V3/V4 codebase and was the first time WebSphere Application Server was coded from a common codebase. Now WAS across all deployment platforms, from Intel x86 to the mainframe, are substantially the same code. The database-based configuration repository was replaced with a replication XML file-based configuration repository. A service called the Deployment Manager had the master copy of the cell configuration, and nodes had the file(s) they needed copied from this master server whenever they changed. V5 also included a miniature version of MQ 5.3 called the embedded Java Message Service (JMS) server.
· Express Edition replaces the Standard Edition. Express now becomes the term to indicate SME-oriented offerings from IBM, across all its software brands.
· Base
· Network Deployment. This version supports deployment of a cell configuration with cluster and J2EE failover support. It now also includes Edge Components, previously known as Edge Server. This provides a proxy server, load balancing, and content-based routing.
· Enterprise Edition. This version added a workflow engine, called the Process Choreographer, for the first time but predates the BPEL standard. It also added the first fully supported application threading model called WebSphere Asynchronous Beans.
· WebSphere Application Server for z/OS. This version is essentially the same as the Network Deployment product but is optimized to take full advantage of z/OS features, such as Workload Manager, to leverage the key technologies that make the mainframe indispensable for mission-critical, scalable, and secure workloads.
Version 5.1 of IBM WebSphere Application Server (WAS).
Released 1 April 2004.
· The main change from V5.0 was a JDK upgrade to 1.4.2 and use of the Jython language for wsadmin scripting support instead of only supporting Java Tcl.
· Express
· Base
· Network Deployment
· WebSphere Application Server for z/OS
Version 5.1 for z/OS is the first to support zAAP engines.
· WebSphere Business Integration Server Foundation V5.1
This is the follow on product to WebSphere Application Server Enterprise Edition V5.0. The workflow engine was updated to support BPEL rather than the proprietary FDML format used in V5.0. The product was also repriced and available on all IBM platforms from the Intel environments to the mainframe.
· WebSphere eXtended Deployment (XD)
For more information please reference the #WebSphere eXtended Deployment section below.
Version 6 of IBM WebSphere Application Server (WAS).
· This version was released on December 31, 2004. It is a Java EE 1.4 compliant application server. Security enhancements include support for JACC 1.0 and WS-Security 1.0.
· Support for Java Standard Edition 1.4
· Community Edition (free, support for fee)
Code based on Apache Geronimo project
· Express (list price US$2,000 per CPU, licensed to use up to two CPUs)
Many programming model extensions previously found in WebSphere Application Server V5.0 Enterprise Edition were moved out of enterprise and into Express and Base. These APIs included application profile, startup beans, the scheduler, and async beans.
The JMS engine, now called "WebSphere Platform Messaging," was rewritten in 100% Java and its functionality greatly enhanced. (WebSphere MQ is still supported as the JMS provider and is interoperable with WebSphere Platform Messaging.)
· Base (list price US$10,000 per CPU)
· Network Deployment (list price US$16,000 per CPU)
The clustering was rewritten to use the high availability manager. This manages all singletons in the WebSphere environment and can provide hot recovery for those singletons.
WebSphere was modified so that a shared file system can be used to store transaction logs and this meant that any cluster member with that shared file system mounted can hot recover in-doubt XA transactions with no external HA software.
The Deployment Manager's role was eliminated from all clustering runtime operations. It's only required for centralized JMX admin and config changes.
Now supports running mixed version cells (V5 to V6) in production.
· WebSphere Application Server for z/OS
Provides the same core functionality as Network Deployment, since it shares a common programming model, but still contains the platform advantages such as:
· z/OS Workload Manager for prioritized management of mixed workloads
· Resource Recovery Services (added transactional integrity for complex, critical transactions)
· Support for security mainframe products such a RACF
· Advanced vertical scaling for application server by featuring a unique control region (integrated control area) server region (where workloads are completed) separation which enables the control region to open and close server regions as needed by the volume of incoming requests
· Parallel Sysplex support for full participation in the Sysplex, enabling advanced failover support and a geographically dispersed environment that seamlessly acts as one with a centralized logging and management facility
· eXtended Deployment (listprice: $16000 USD / cpu)
WAS XD as it is known increases the functionality of the application server in two main areas - Manageability and Performance. It also allows makes possible new configurations, such as dynamic virtualization between pools of application servers.
Under the performance header the ObjectGrid component was added, which is a standalone distributed cache that can be used with any application server (any version with a 1.4 JDK) or with any J2SE 1.4 runtime, including zLinux and z/OS support.
With Version 6, some of the functionality previously found in WebSphere Business Integration Server Foundation (WBISF) moved into the new IBM WebSphere Process Server. Other function moved into the other editions (Express and above).
Version 6.1 of IBM WebSphere Application Server (WAS).
This version was released on June 30, 2006. It is a Java EE 1.4 compliant application server and includes the following function:
· Support for Java Standard Edition 1.5
· Support for running JSR 168 Portlets in the application server
· Session Initiation Protocol (SIP) Servlets
· Enhancements to the WebSphere Install Factory
· IBM Support Assistant
· IBM JSF Widget Library
· Simplified Administration
· Improved Certificate and Key Management
· Security Enhancements
· Administration of IBM HTTP Server from WebSphere Admin Console
· Support for Web Services Resource Framework and WS-BusinessActivity (WS-BA)
· Support for JSR160 JMX Remote Connections (From IBM Agents Only)
· Administrative Console Jython Command Assistance
· Enhanced scripting. This version started the deprecation process for the Jacl syntax.[1]
· 64-bit servants and a new Apache-based IBM HTTP Server for z/OS
Support for the EJB 3.0 technology and support for some webservices standards were provided by the EJB feature pack and the webservices feature packs, respectively. These function in these feature packs has been folded into the main product in version 7. Functions in the webservices feature pack include:
· Asynchronous programming model (Limited functional support)
· Multiple Payload structures
· StAX (Streaming API for XML)
· WS-RM (Limited functional support)
· WS-Addressing (Limited functional support)
· JAX-B support
· Policy Set (Limited functional support)
· Secured thin client (Limited functional support)
· SOAP (protocol) Message Transmission Optimization Mechanism (MTOM)
· Supports CGI and CORBA
Version 7 of IBM WebSphere Application Server (WAS).
· This version was released on September 9, 2008. It is a Java EE 5 compliant application server.
Following are the flagship features of WebSphere Application Server Version 7:
· Flexible Management
Flexible Management facilitate administration of a large number of WebSphere Application Server base edition and Network Deployment topologies that might be geographically distributed.
· Business-Level Application
Business-Level Application is used for managing application artifacts independent of packaging or programming models.
· Property Based Configuration
Property Based Configuration feature simplifies the experience of automating administration, administrator can update the WebSphere Application Server Version 7 configuration using simple property file.
WebSphere Extended Deployment
WebSphere Application Server V6 Extended Deployment Edition (WebSphere XD) was released in 2006 as an add-on for WebSphere 6. XD provides advanced features for both administrators who manage multiple Java EE-based applications and developers building advanced applications that require asymmetric clustering techniques. It also has a number of technologies to significantly increase the performance of running applications, including an in-memory database cache and a highly advanced load balancer called the on demand router.
Administrator benefits
Many businesses run multiple server farms but wish to consolidate them into a single smaller server farm. This is because most server farms are underutilizied or over provisioned. The boxes are typically running at 10% load which is quite costly and is not flexible. For example, one server farm goes hot and maxes out while the farm in the next room is still basically idle at 10%. XD allows administrators to define a single cluster (a node group) then monitor the workload and dynamically decide which boxes in the node group should host which application in order to meet these goals. If application A has a current response time of 1.5 seconds, XD will move resources away from applications B and C to increase the power dedicated to A and decrease its response time. XD can also predict that A will likely exceed its response time in 10 minutes based on a trend and react in anticipation of the event. This greatly simplifies the life of an administrator and allows the machines to be more efficiently used than a conventional multiple, independent farm of farms approach. XD also offers options to generate various email alerts when conditions are exceeded. It can also restart servers when they appear to have a memory leak, or after X requests.
Developer benefits
WebSphere Partition Facility
Traditional Java EE applications work well for a large class of applications. The class can be broadly categorized as applications that run in a stateless symmetric cluster in front of a database:
· All the cluster members can perform any task at any time.
· The application is stateless.
· The application is modal, such that it only performs work synchronously in response to a client request which can be received using http://IIOP or JMS.
There are other applications that do not work well in such an environment, for example, an electronic trading system in a bank. Such applications typically use performance enhancing techniques such as partitioning, multi-threading, and write-through caching. These are applications that can exploit asymmetric clustering. An asymmetric cluster is essentially the opposite of a symmetric cluster:
· Applications can declare named partitions at any point while they are running, partitions are highly available, mobile within the cluster, and usually only run on a single cluster member at a time.
· Incoming work for a partition is routed to the cluster member hosting the partition.
· The application is amodal. Partitions have a lifecycle of their own and can start background threads or alarms as well as respond to incoming events whether they are IIOP/HTTP or JMS/foreign messages.
WebSphere XD offers a new set of APIs called the WebSphere Partition Facility (WPF). These APIs allow applications that require an asymmetric cluster to be deployed on a Java EE server.
ObjectGrid
The ObjectGrid is the first piece of the IBM distributed caching framework. V6 of XD shipped with support for local Java object caching as well as peer-to-peer caching with asynchronous data push/invalidation. It is designed as a small footprint, to install customer extensible framework for caching objects. All aspects of the core framework have plugin points. This allows customers to add function as well as allow IBM to extend it in future product levels. It is designed to run independent of WebSphere. This does not mean it won't integrate with WebSphere 6.0 XD -- it will. But it will also work on older versions of the application server, Tomcat servers, and competitive application servers. In a very limited sense, memcached performs some of the same functions as ObjectGrid[2]
ObjectGrid is intended to compete against the other distributed cache products on the market. It currently requires only a 1.4 level JDK from any vendor. Version 2 of the ObjectGrid is currently under development for shipping in XD 6.0.1. It will add significant function to the component as well as widen JDK level support. The intent is to allow customers to build large grids of JVMs into which they can connect applications and store objects at various qualities of service. The grid is being designed to scale to thousands of JVMs and hold a large quantity of data.
Compute Grid
Also known as WebSphere Batch, WebSphere XD also offers a Java Batch processing system called Compute Grid. This was first introduced in XD version 6.1. Compute Grid is deployed as an additional feature of a WebSphere Network environment. It provides a number of features that help you create, execute and manage batch jobs. The features include: an XML-based job control language (xJCL), batch programming model, job scheduler, and batch container.
Security
The WebSphere Application Server security model is based on the services provided in the operating system and the Java EE security model. WebSphere Application Server provides implementations of user authentication and authorization mechanisms providing support for various user registries:
· Local operating system user registry
· LDAP user registry
· Federated user registry (as of version 6.1)
· Custom user registry
The authentication mechanisms supported by WebSphere are [3]
· Lightweight Third Party Authentication (LTPA)
Saturday, March 7, 2009
What is WebSEAL
IBM(R)Tivoli(R)Access Manager for e-business (Tivoli Access Manager) is a robust and secure centralized policy management solution for e-business and distributed applications. IBM Tivoli Access Manager WebSEAL is a high performance, multi-threaded Web server that applies fine-grained security policy to the Tivoli Access Manager protected Web object space. WebSEAL can provide single sign-on (SSO) solutions and incorporate back-end Web application server resources into its security policy.
IBM Tivoli Access Manager:
IBM Tivoli Access Manager is a complete authorization and network security policy management solution that provides unsurpassed end-to-end protection of resources over geographically dispersed intranets and extranets.
In addition to its state-of-the-art security policy management feature, Tivoli Access Manager provides authentication, authorization, data security, and centralized resource management capabilities. You use Tivoli Access Manager in conjunction with standard Internet-based applications to build highly secure and well-managed intranets.
At its core, Tivoli Access Manager provides:
Authentication framework
Tivoli Access Manager provides a wide range of built-in authenticators and supports external authenticators.
Authorization framework
The Tivoli Access Manager authorization service, accessed through the Tivoli Access Manager authorization API, provides permit and deny decisions on requests for protected resources located in the secure domain.
With Tivoli Access Manager, businesses can securely manage access to private internal network-based resources while leveraging the public Internet's broad connectivity and ease of use. Tivoli Access Manager, in combination with a corporate firewall system, can fully protect the Enterprise intranet from unauthorized access and intrusion.
IBM Tivoli Access Manager WebSEAL:
IBM Tivoli Access Manager WebSEAL is the resource manager responsible for managing and protecting Web-based information and resources.
WebSEAL is a high performance, multi-threaded Web server that applies fine-grained security policy to the Tivoli Access Manager protected Web object space. WebSEAL can provide single sign-on solutions and incorporate back-end Web application server resources into its security policy.
WebSEAL normally acts as a reverse Web proxy by receiving HTTP/HTTPS requests from a Web browser and delivering content from its own Web server or from junctioned back-end Web application servers. Requests passing through WebSEAL are evaluated by the Tivoli Access Manager authorization service to determine whether the user is authorized to access the requested resource.
WebSEAL provides the following features:
Supports multiple authentication methods
Both built-in and plug-in architectures allow flexibility in supporting a variety of authentication mechanisms.
Accepts HTTP and HTTPS requests
Integrates and protects back-end server resources through WebSEAL junction technology
Manages fine-grained access control for the local and back-end server Web space
Supported resources include URLs, URL-based regular expressions, CGI programs, HTML files, Java servlets, and Java class files.
Performs as a reverse Web proxy
WebSEAL appears as a Web server to clients and appears as a Web browser to the junctioned back-end servers it is protecting.
Provides single sign-on capabilities
Thursday, March 5, 2009
Overview on the Caching Proxy, WebSphere Edge Components.
In an enterprise environment, a proxy server is a server that acts as an intermediary, typically placed in a demilitarized zone (DMZ). This DMZ is between the Internet and the server environment in the internal zone, providing the business services. It validates the request for an Internet service.
If the request passes filtering requirements, the proxy server forwards it to servers in the internal (secure) zone and acts as the requester. This mechanism prevents direct access from the (insecure external zone) to the sensitive servers in the internal zone .
The proxy servers used here can also improve performance by caching content locally.
The two main advantages of using a proxy server are system security and performance:
Security: A proxy server provides an additional layer of security and can protect HTTP servers further up the chain. It intercepts requests from the client, retrieves the requested information from the content-hosting machines, and delivers that information back to the client. If you are using a firewall between the reverse proxy server and the content HTTP server, you can configure the firewall to allow only HTTP requests from the proxy server.
Performance: A proxy server can increase the performance of your WebSphere Application Server in several ways.
Encryption/SSL acceleration: You can equip the proxy server with SSL acceleration hardware that can improve the performance of SSL requests.
Caching: The proxy server can cache static content to provide better performance.
Load balancing: The proxy server can balance the workload among several content HTTP servers.
WebSphere Edge Components Caching Proxy (CPS)
The WebSphere Edge Component Caching Proxy reduces bandwidth usage and improves a Web site's speed and reliability by providing a point-of-presence node for one or more backend content servers. Caching Proxy can cache and serve static content and content dynamically generated by WebSphere Application Server.
The proxy server intercepts data requests from a client, retrieves the requested information from content-hosting machines, and delivers that content back to the client. Most commonly, the requests are for documents stored on Web server machines (also called origin servers or content hosts) and delivered using the Hypertext Transfer Protocol (HTTP). However, you can configure the proxy server to handle other protocols, such as File Transfer Protocol (FTP) and Gopher.
The proxy server stores cache-able content in a local cache before delivering it to the requester. Examples of cache-able content include static Web pages and
JavaServer Pages files that contain dynamically generated, but infrequently changing, information. Caching enables the proxy server to satisfy subsequent requests for the same content by delivering it directly from the local cache, which is much quicker than retrieving it again from the content host.
There are several plugins for the Caching Proxy and for additional functionality to the proxy server, but we used only the default setup.
WebSphere Proxy Server (PS)
WebSphere Proxy Server (PS) is a new type of server supported in WebSphere Application Server Network Deployment (ND) package (in version 6.0.2 and later). This Proxy server receives requests from clients initially on behalf of content servers and work load manages, and routes the requests across content servers depending on the policies and filter classification definitions.
WebSphere Proxy servers can secure the transport (using SSL), content and protect the identity of application servers using the response transformation feature (URL rewriting). The Proxy server can also cache responses to improve throughput and performance. Another good feature to note is SSL offload at the Proxy server. When using this feature you can terminate an SSL (HTTPS) connection at the proxy server after receiving the request from the client and use HTTP as transport protocol between proxy server and the content server(s) (which are application server(s)). You can administer and configure this Proxy server from the deployment manager's administrator console (or wsadmin) in an ND environment.
This Proxy server is much more capable than the reverse proxy servers (the Edge caching server and the WebSphere plugin) with its advanced configuration capabilities, dynamic routing policies, and integrated system management in ND topology.
It is interesting to note that the Proxy server can also route requests across multiple cells and supports session affinity and failover.
Tuesday, February 24, 2009
What Is Single Sign-On, What Is Kerberos
In spite of its perfectly descriptive nature, "single sign-on" is a frequently
misused term. SSO means, literally, that you only need to provide a
username and password once and that, subsequently, software will
recognize your established credentials and not prompt for them again.
The "single" part of SSO is typically satisfied when a user first logs in to a
computer. The user types his/her username and password and
establishes a set of credentials that are then respected by software that
is aware of the SSO mechanism.
"Single username/password" is not SSO. Having a single username
name and password that is synchronized across multiple systems but
have to be, occasionally, re-entered is not SSO. Similarly, password
caches or password key rings are also not examples of SSO. Key rings
are essentially "typing aids" that automatically enter passwords for you;
they do not reflect an authentication infrastructure that understands SSO.
When SSO is provided across an entire network of computers and
applications, it is often referred to as enterprise single sign-on. This is the
most valuable form of SSO and the one that this document explores.
References to "SSO" should be understood to apply across the
enterprise.
What Is Kerberos
Kerberos is an authentication protocol that facilitates the implementation
of SSO. It was developed at MIT in the late 1980's as part of the Athena
project. It was originally described in RFC 1510 but its modern
incarnation is described by RFC 4120.
Kerberos is an accepted standard for SSO. It is considered a secure
authentication mechanism, having been designed to withstand common
network attacks (for example, man-in-the-middle and replay attacks). It is
available on all modern operating systems and supported by many
software applications. Microsoft has supported Kerberos since the
advent of Microsoft WindowsÔ 2000.
Kerberos uses encrypted tickets to represent credentials.
• The encryption technique relies on a shared secret (a key) known
to the Kerberos client and the Kerberos key distribution center
(KDC). This secret is based on an account password. When a
user account is created at the KDC, Kerberos stores the shared
secret and uses it to encrypt tickets sent to a client on behalf of
the user. When the user logs into the client machine, he/she
provides a username and password, establishing the shared
secret on the client as well. This allows the KDC and client
machines to communicate in a safe, encrypted, fashion.
• Applications that want to use Kerberos will need to be associated
with service accounts that establish shared secrets on the KDC.
This allows the KDC to encrypt tickets in a form that can only be
understood by relevant applications.
• User and applications keys (shared secrets) are usually stored in
a key table (keytab) for subsequent use. These keytabs need to
be available to software that needs them to decrypt Kerberos
data. A user's keytab should be established when the user logs
into to a computer. Application keytabs are longer-lived and are
only created when passwords are changed on service accounts.
• When a user needs to access a Kerberized application, he/she
(indirectly, via a client application) asks the KDC for a service
ticket for that application. A portion of this ticket is encrypted with
the user's shared secret and another portion is encrypted with the
application's shared secret. This allows both the user's client
computer and the application's client computer to verify that the
incoming ticket is valid.
• Kerberized applications frequently support other forms of
authentication and make it necessary for application clients to
negotiate what type of authentication they're going to perform.
Operating systems typically provide software to facilitate this
negotiation. Windows systems provide SSPI whereas Linux/UNIX
provide GSSAPI. These two systems are, mostly, interoperable.
Although Kerberos facilitates the implementation of SSO, it can be
extremely difficult and frustrating to get it to work properly. Many
individual steps are involved and mistakes anywhere along the way
typical only manifest themselves by a failure of authentication (SSO
doesn't SO!). It can be difficult to diagnose where errors might have crept
into the process.
Friday, January 16, 2009
vi Editor Commands
General Startup
Counts
Cursor Movement
Screen Movement
Inserting
Deleting
Copying Code
Put Command
Find Commands
Miscellaneous Commands
Line Editor Mode
ex Commands
Substitutions
Reading Files
Write File
Moving
Shell Escape
General Startup
To use vi: vi filename
To exit vi and save changes: ZZ or :wq
To exit vi without saving changes: :q!
To enter vi command mode: [esc]
Counts
A number preceding any vi command tells vi to repeat
that command that many times.
Cursor Movement
h move left (backspace)
j move down
k move up
l move right (spacebar)
[return] move to the beginning of the next line
$ last column on the current line
0 move cursor to the first column on the
current line
^ move cursor to first nonblank column on the
current line
w move to the beginning of the next word or
punctuation mark
W move past the next space
b move to the beginning of the previous word
or punctuation mark
B move to the beginning of the previous word,
ignores punctuation
e end of next word or punctuation mark
E end of next word, ignoring punctuation
H move cursor to the top of the screen
M move cursor to the middle of the screen
L move cursor to the bottom of the screen
Screen Movement
G move to the last line in the file
xG move to line x
z+ move current line to top of screen
z move current line to the middle of screen
z- move current line to the bottom of screen
^F move forward one screen
^B move backward one line
^D move forward one half screen
^U move backward one half screen
^R redraw screen
( does not work with VT100 type terminals )
^L redraw screen
( does not work with Televideo terminals )
Inserting
r replace character under cursor with next
character typed
R keep replacing character until [esc] is hit
i insert before cursor
a append after cursor
A append at end of line
O open line above cursor and enter append mode
Deleting
x delete character under cursor
dd delete line under cursor
dw delete word under cursor
db delete word before cursor
Copying Code
yy (yank)'copies' line which may then be put by
the p(put) command. Precede with a count for
multiple lines.
Put Command
brings back previous deletion or yank of lines,
words, or characters
P bring back before cursor
p bring back after cursor
Find Commands
? finds a word going backwards
/ finds a word going forwards
f finds a character on the line under the
cursor going forward
F finds a character on the line under the
cursor going backwards
t find a character on the current line going
forward and stop one character before it
T find a character on the current line going
backward and stop one character before it
; repeat last f, F, t, T
Miscellaneous Commands
. repeat last command
u undoes last command issued
U undoes all commands on one line
xp deletes first character and inserts after
second (swap)
J join current line with the next line
^G display current line number
% if at one parenthesis, will jump to its mate
mx mark current line with character x
'x find line marked with character x
NOTE: Marks are internal and not written to the file.
Line Editor Mode
Any commands form the line editor ex can be issued
upon entering line mode.
To enter: type ':'
To exit: press[return] or [esc]
ex Commands
For a complete list consult the
UNIX Programmer's Manual
SUBSTITUTION__:#,#s/old/new">READING FILESSUBSTITUTION__:#,#s/old/new'">
SUBSTITUTION__:#,#s/old/new'"> copies (reads) filename after cursor in file
SUBSTITUTION__:#,#s/old/new'"> currently editing
SUBSTITUTION__:#,#s/old/new'">
SUBSTITUTION__:#,#s/old/new'"> :r filenameSUBSTITUTION__:#,#s/old/new'">
:w saves the current file without quitting
MOVING
:# move to line #
:$ move to last line of file
SHELL ESCAPE
executes 'cmd' as a shell command.
:!'cmd'
Thursday, January 15, 2009
WebSphere Application server Tuning Tips for IBM AIX, Sun SOLARIS, Microsoft Windows.
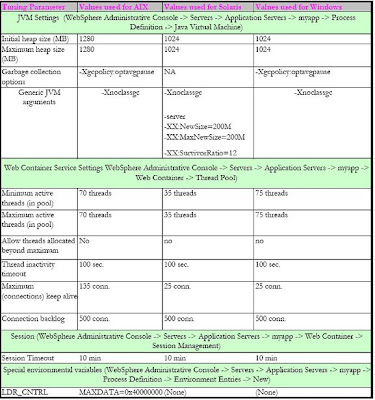
Session timeout 10 minutes The default value of Session Timeout is 30 minutes. Reducing this value to a lower number can help reduce memory consumption requirements, allowing a higher user load to be sustained for longer periods of time. Reducing the value too low can interfere with the user experience. Please determine this based on your end user requirements: if they mostly have quick tasks to finish, set this low; if they have long tasks to finish, set this higher.
Thursday, January 8, 2009
APTITUDE QUESTIONS for Project Managers
1.A three digit number consists of 9,5 and one more number . When these digits are reversed and
then subtracted from the original number the answer yielded will be consisting of the same digits
arranged yet in a different order. What is the other digit?
Sol. Let the digit unknown be n.
The given number is then 900+50+n=950+n.
When reversed the new number is 100n+50+9=59+100n.
Subtracting these two numbers we get 891-99n.
The digit can be arranged in 3 ways or 6 ways.
We have already investigated 2 of these ways.
We can now try one of the remaining 4 ways. One of these is n 95
100n+90+5=891-99n
or 199n =796
so, n=4
the unknown digit is 4.
2.A farmer built a fence around his 17 cows,in a square shaped region.He used 27 fence poles on
each side of the square. How many poles did he need altogether???
Ans.104 poles
Sol. Here 25 poles Must be there on each side .And around four corners 4 poles will be
present. 4*25+4=100+4=104 poles.
3.On the first test of the semester, kiran scored a 60. On the last test of the semester, kiran scored
75%
By what percent did kiran's score improve?
Ans: 25%
Sol. In first test kiran got 60
In last test he got 75.
% increase in test ( 60(x+100))/100=75
0.6X+60=75
0.6X=15
X=15/0.6=25%
4.A group consists of equal number of men and women. Of them 10% of men and 45% of women are
unemployed. If a person is randomly selected from the group. Find the probability for the selected person to
be an employee.
Ans:29/40
Sol: Assume men=100,women=100 then employed men & women r (100-10)+(100-45)=145
So probability for the selected person to be an employee=145/200=29/40
5. Randy's chain of used car dealership sold 16,400 cars in 1998. If the chain sold 15,744 cars in
1999, by what percent did the number of cars sold decrease?
Ans: 4%
Sol. Let percentage of decrease is x , then
16400(100-x)/100=15744
16400-15744=164x
x=656/164=4%
6. A radio when sold at a certain price gives a gain of 20%. What will be the gain percent, if sold for thrice the
price?
A) 260%
B) 150%
C) 100%
D) 50%
E) None of these
Ans: 260%
Sol. Let x be original cost of the radio.
The solding price = (100+20)x=120x
If , it is sold for thrice the price ,then 3*120x=360x
So, gain percent is (360-100)=260%.
7. Find the perimeter of the shape below.
Ans: 24cm
Sol: 2+4+5+1+7+5=24
8.If the Arithmetic mean is 34 and geometric mean is 16 then what is greates number in that series of
numbers?
Ans. 64
Sol. Let two numbers be x, y;
Arthmetic mean=34=>( x+y)/2=34
x+y=68
geometric mean=16=>(xy)pow 1/2=16
5cm
4cm
1cm
2cm
xy=16*16=256
By trail and error 16*16=64*4
And 64+4/2=34
So the greatest number int hat series is 64.
9. The diameter of the driving wheel of a bus is 140cm. How many revolutions per minute must the wheel
make in order to keep a speed of 66 kmph?
Ans. 250
Sol. Distance to be covered in 1 min=(66*1000)/60 m=1100m
Circumference of the wheel =(2*22/7*0.70)m=4.4m.
So, Number of revolutions per min=1100/4.4=250.
10. The boys and girls in a college are in the ratio 3:2. If 20% of the boys and 25% of the girls are adults, the
percentage of students who are not adults is:??
Ans.78%
Sol: Suppose boys = 3x and girls = 2x
Not adults = (80*3x/100) + (75*2x/100) = 39x/10
Required percentage = (39x/10)*(1/5x)*100 = 78%
11. Vivek travelled 1200km by air which formed 2/5 of his trip.One third of the whole trip , he travelled by
car and the rest of the journey he performed by train. The distance travelled by tain was???
Ans.800km
Sol: Let the total trip be x km.
Then 2x/5=1200
x=1200*5/2=3000km
Distance travelled by car =1/3*3000=1000km
Journey by train =[3000-(1200+1000)]=800km.
12. In a college ,1/5 th of the girls and 1/8 th of the boys took part in a social camp.What of the total number
of students in the college took part in the camp?
Ans: 2/13
Sol: Out of 5 girls 1 took part in the camp
out of 8 boys 1 took part in the camp
so, out of 13 students 2 took part in the camp.
So, 2/13of the total strength took part in the camp.
13. On sports day,if 30 children were made to stand in a column,16 columns could be formed. If 24 children
were made to stand in a column , how many columns could be formed?
Ans. 20
Sol: Total number of children=30*16=480
Number of columns of 24 children each =480/24=20.
14. Two trains 200mts and 150mts are running on the parallel rails at this rate of 40km/hr and 45km/hr.In
how much time will they cross each other if they are running in the same direction.
Ans: 252sec
Sol: Relative speed=45-40=5km/hr=25/18 mt/sec
Total distance covered =sum of lengths of trains =350mts.
So, time taken =350*18/25=252sec.
15. 5/9 part of the population in a village are males. If 30% of the males are married, the percentage of
unmarried females in the total population is:
Ans: (250/9)%
Sol: Let the population =x Males=(5/9)x
Married males = 30% of (5/9)x = x/6
Married females = x/6
Total females = (x-(5/9)x)=4x/9
Unmarried females = (4x/9 – x/6) = 5x/18
Required percentage = (5x/18 * 1/x * 100) = (250/9)%
16. From height of 8 mts a ball fell down and each time it bounces half the distnace back. What will be the
distance travelled
Ans.: 24
Sol. 8+4+4+2+2+1+1+0.5+0.5+ and etc .. =24
17. First day of 1999 is sunday what day is the last day
Ans.: Monday
18. Increase area of a square by 69% by what percent should the side be incresed
Ans.: 13
Sol:Area of square=x2
Then area of increase=100+69=169
square root of 169 i.e 13 .
19. Ten years ago, chandrawathi’s mother was four times older than her daughter. After 10years, the mother
will be twice older than daughter. The present age of Chandrawathi is:
Ans.20 years
Sol: Let Chandrawathi’s age 10 years ago be x years.
Her mother’s age 10 years ago = 4x
(4x+10)+10=2(x+10+10)
x=10
Present age of Chandrawathi = (x+10) = 20years
20. Finding the wrong term in the given series
7, 28, 63, 124, 215, 342, 511
Ans:28
Sol: Clearly, the correct sequence is
2^3 – 1, 3^3 – 1, 4^3 – 1, 5^3 – 1, ……….
Therefore, 28 is wrong and should be replaced by (3^3 – 1) i.e, 26.
21. If a man walks at the rate of 5kmph, he misses a train by only 7min. However if he walks at the
rate of 6 kmph he reaches the station 5 minutes before the arrival of the train.Find the distance
covered by him to reach the station.
Ans:6km.
Sol: Let the required distance be x km.
Difference in the times taken at two speeds=12mins=1/5 hr.
Therefore x/5-x/6=1/5 or 6x-5x=6 or x=6km.
Hence ,the required distance is 6 km
22. Walking 5/6 of its usual speed, a train is 10min late. Find the usual time to cover the journey?
Ans:50 min
Sol: New speed = 5/6 of usual speed
New time = 6/5 of usual time
Therefore, (6/5 of usual time) – usual time = 10min
Therefore Usual time = 50min
23.A train running at 54 kmph takes 20 seconds to pass a platform. Next it takes 12 seconds to pass
a man walking at 6 kmph in the same direction in which the train is going. Find the length of the
train and the length of the platform.
Ans. length of the train=160m
length of the platform=140 m.
Sol: Let the length of the train be x meters and length of the platform be y meters.
Speed of the train relative to man=(54-6) kmph =48 kmph.
=(48*5/18) m/sec =40/3 m/sec.
In passing a man, the train covers its own length with relative speed.
Therefore, length of the train=(Relative speed *Time)
=(40/3 * 12) m =160 m.
Also, speed of the train=(54 * 5/18) m/sec=15 m/sec.
Therefore, x+y/2xy=20 or x+y=300 or y=(300-160 m=140 m.
Therefore, Length of the platform=140 m.
24. A man is standing on a railway bridge which is 180m long. He finds that a train crosses the
bridge in 20seconds but himself in 8 seconds. Find the length of the train and its speed.
Ans: length of train=120m
Speed of train=54kmph
Sol: Let the length of the train be x meters
Then, the train covers x meters in 8 seconds and (x + 180) meters in 20 seconds.
Therefore x/8 = (x+180)/20 ó 20x = 8(x+180) ó x = 120
Therefore Length of the train = 120m
Speed of the train = 120/8 m/sec = 15 m/sec =15 * 18/5 kmph = 54kmph
25. A man sells an article at a profit of 25%. If he had bought it at 20 % less and sold it for Rs.10.50
less, he would have gained 30%. Find the cost price of the article?
Ans. Rs. 50.
Sol: Let the C.P be Rs.x.
1st S.P =125% of Rs.x.= 125*x/100= 5x/4.
2nd C.P=80% of x. = 80x/100 =4x/5.
2nd S.P =130% of 4x/5. = (130/100* 4x/5) = 26x/25.
Therefore, 5x/4-26x/25 = 10.50 or x = 10.50*100/21=50.
Hence, C.P = Rs. 50.
26. A grosser purchased 80 kg of rice at Rs.13.50 per kg and mixed it with 120 kg rice at Rs. 16 per
kg. At what rate per kg should he sell the mixture to gain 16%?
Ans: Rs.17.40 per kg.
Sol: C.P of 200 kg of mix. = Rs (80*13.50+120*16) = Rs.3000.
S.P = 116% of Rs 3000= Rs (116*3000/100) = Rs.3480.
Rate of S.P of the mixture = Rs.3480/200.per kg. = Rs.17.40 per kg.
27. Two persons A and B working together can dig a trench in 8 hrs while A alone can dig it in 12
hrs. In how many hours B alone can dig such a trench?
Ans:24hours.
Sol: (A+B)’s one hour’s work =1/8, A’s one hour’s work =1/12
Therefore, B’s one hour’s work = (1/8-1/12) =1/24.
Hence, B alone can dig the trench in 24 hours.
28. A and B can do a piece of work in 12 days ; B and C can do it in 20 days. In how many days will
A, B and C finishes it working all together?
Also, find the number of days taken by each to finish it working alone?
Ans:60 days
Sol: (A+B)’s one day’s work=1/12; (B+C)’s one day’s work=1/15 and (A+C)’s one day’s
work=1/20.
Adding, we get: 2(A+B+C)’s one day’s work = (1/12+1/15+1/20)=1/5.
Therefore, (A+B+C)’s one day’s work=1/10.
Thus, A, B and C together can finish the work in 10 days.
Now, A’s one day’s work
= [(A+B+C)’s one day’s work] – [(B+C)’s one day’s work]
= 1/10-1/15)
= 1/30.
Therefore, A alone can finish the work in 30 days.
Similarly, B’s 1 day’s work = (1/10 -1/20) = 1/20.
Therefore, B alone can finish the work in 20 days.
And, C’s 1 day’s work= (1/10-1/12) = 1/60.
Therefore, C alone can finish the work in 60 days.
29. A is twice as good a workman as B and together they finish a piece of work in 18
days.In how many days will A alone finish the work?
Ans:27 days.
Sol: (A’s 1 day’s work): (B’s 1 day’s work) = 2:1.
(A + B)’s 1 day’s work = 1/18.
Divide 1/18 in the ratio 2:1.
Therefore A’s 1 day’s work = (1/18 * 2/3) = 1/27.
Hence, A alone can finish the work in 27 days.
30. 2 men and 3 boys can do a piece of work in 10 days while 3 men and 2 boys can do the same
work in 8 days. In how many days can 2 men and 1 boy do the work?
Ans: 12 ½ days.
Sol: Let 1 man’s 1 day’s work = x and 1 boy’s 1 day’s work =y.
Then, 2x+3y=1/10 and 3x+2y=1/8.
Solving, we get: x=7/200 and y=1/100.
Therefore (2 men +1 boy)’s 1 day’s work = (2*7/200 + 1*1/100) = 16/200 = 2/25.
So, 2 men and 1 boy together can finish the work in 25/2 =12 ½ days.
31. What was the day of the week on 12th January, 1979?
Ans: Friday
Sol: Number of odd days in (1600 + 300) years = (0 + 1) = 1 odd day.
78 years = (19 leap years + 59 ordinary years) = (38 + 59) odd days = 6 odd days
12 days of January have 5 odd days.
Therefore, total number of odd days= (1 + 6 + 5) = 5 odd days.
Therefore, the desired day was Friday.
32. Find the day of the week on 16th july, 1776.
Ans: Tuesday
Sol: 16th july, 1776 means = 1775 years + period from 1st january to 16th july
Now, 1600 years have 0 odd days.
100 years have 5 odd days.
75 years = 18 leap years + 57 ordinary years
= (36 + 57) odd days = 93 odd days
= 13 weeks + 2 odd days = 2 odd days
Therefore, 1775 years have (0 + 5 + 2) odd days = 0 odd days.
Now, days from 1st Jan to 16th july; 1776
Jan Feb March April May June July
31 + 29 + 31 + 30 + 31 + 30 + 16 = 198 days
= (28 weeks + 2 days) odd days
Therefore, total number of odd days = 2
Therefore, the day of the week was Tuesday
33 .Find the angle between the minute hand and hour hand of a click when the time is
7.20?
Ans: 100deg
Sol: Angle traced by the hour hand in 12 hours = 360 degrees.
Angle traced by it in 7 hrs 20 min i.e. 22/3 hrs = [(360/12) * (22/3)] = 220 deg.
Angle traced by minute hand in 60 min = 360 deg.
Angle traced by it in 20 min = [(360/20) * 60] = 120 deg.
Therefore, required angle = (220 - 120) = 100deg.
34.The minute hand of a clock overtakes the hours hand at intervals of 65 min of the correct time.
How much of the day does the clock gain or lose?
Ans: the clock gains 10 10/43 minutes
Sol: In a correct clock, the minute hand gains 55 min. spaces over the hour hand in 60
minutes.
To be together again, the minute hand must gain 60 minutes over the hour hand.
55 minutes are gained in 60 min.
60 min. are gained in [(60/55) * 60] min == 65 5/11 min.
But they are together after 65 min.
Therefore, gain in 65 minutes = (65 5/11 - 65) = 5/11 min.
Gain in 24 hours = [(5/11) * (60*24)/65] = 10 10/43 min.
Therefore, the clock gains 10 10/43 minutes in 24 hours.
35.A clock is set right at 8 a.m. The clock gains 10 minutes in 24 hours. What will be the true time
when the clock indicates 1 p.m. on the following day?
Ans. 48 min. past 12.
Sol: Time from 8 a.m. on a day to 1 p.m. on the following day = 29 hours.
24 hours 10 min. of this clock = 24 hours of the correct clock.
145/6 hrs of this clock = 24 hours of the correct clock.
29 hours of this clock = [24 * (6/145) * 29] hrs of the correct clock
= 28 hrs 48 min of the correct clock.
Therefore, the correct time is 28 hrs 48 min. after 8 a.m.
This is 48 min. past 12.
36. At what time between 2 and 3 o’ clock will the hands 0a a clock together?
Ans: 10 10/11 min. past 2.
Sol: At 2 o’ clock, the hour hand is at 2 and the minute hand is at 12, i.e. they are 10
min space apart.
To be together, the minute hand must gain 10 minutes over the other hand.
Now, 55 minutes are gained by it in 60 min.
Therefore, 10 min will be gained in [(60/55) * 10] min = 10 10/11 min.
Therefore, the hands will coincide at 10 10/11 min. past 2.
37. A sum of money amounts to Rs.6690 after 3 years and to Rs.10035 after 6 years on compound
interest. Find the sum.
Ans: Rs. 4460
Sol: Let the Sum be Rs. P. Then
P [1 + (R/100)]^3 = 6690………..(i)
P [1 + (R/100)]^6 = 10035………..(ii)
On dividing, we get [1 + (R/100)]^3 = 10035/6690 = 3/2.
P * (3/2) = 6690 or P = 4460.
Hence, the sum is Rs. 4460.
38. Simple interest on a certain sum is 16/25 of the sum. Find the rate percent and time, if both are
numerically equal.
Ans: Rate = 8% and Time = 8 years
Sol: Let sum = X. Then S.I. = 16x/25
Let rate = R% and Time = R years.
Therefore, x * R * R/100 = 16x/25 or R^2 = 1600/25, R = 40/5 = 8
Therefore, Rate = 8% and Time = 8 years.
39. Find
i. S.I. on RS 68000 at 16 2/3% per annum for 9 months.
ii. S.I. on RS 6250 at 14% per annum for 146 days.
iii. S.I. on RS 3000 at 18% per annum for the period from 4th Feb 1995 to 18th
April 1995.
Ans: i. RS 8500.
ii. RS 350.
iii. RS 108.
Sol:
i. P = 68000, R = 50/3% p.a. and T = 9/12 year = ¾ years
Therefore, S.I. = (P * Q * R/100)
= RS (68000 * 50/3 * ¾ * 1/100) = RS 8500.
ii. P = RS 6265, R = 14% p.a. and T = (146/365) year = 2/5 years.
Therefore, S.I. = RS (6265 * 14 * 2/5 *1/100) = RS 350.
iii. Time = (24 + 31 + 18) days = 73 days = 1/5 year
P = RS 3000 and R = 18% p.a.
Therefore, S.I. = RS (3000 * 18 * 1/5 * 1/100) = RS 108
40. A sum at simple interest at 13 ½% per annum amounts to RS 2502.50 after 4 years. Find the
sum.
Ans: sum = RS 1625
Sol: Let sum be x. Then,
S.I. = (x * 27/2 * 4 * 1/100) = 27x/50
Therefore, amount = (x + 27x/50) = 77x/50
Therefore, 77x/50 = 2502.50 or x = 2502.50 * 50 / 77 = 1625
Hence, sum = RS 1625
41. A sum of money doubles itself at C.I. in 15 years. In how many years will it become eight times?
Ans.45 years.
Sol: P [1 + (R/100)]^15 = 2P è [1 + (R/100)]^15 = 2……….(i)
Let P [1 + (R/100)]^n = 8P è P [1 + (R/100)]^n = 8 = 2^3
= [{1 + (R/100)}^15]^3.
è [1 + (R/100)]^n = [1 + (R/100)]^45.
è n = 45.
Thus, the required time = 45 years.
42. A certain sum amounts to Rs. 7350 in 2 years and to Rs. 8575 in 3 years. Find the sum and rate
percent.
Ans: Sum = Rs. 5400,Rate=16 2/3 %.
Sol: S.I. on Rs. 7350 for 1 year = Rs. (8575-7350) = Rs. 1225.
Therefore, Rate = (100*1225 / 7350*1) % = 16 2/3 %.
Let the sum be Rs. X. then, x[1 + (50/3*100)]^2 = 7350.
è x * 7/6 * 7/6 = 7350.
è x = [7350 * 36/49] = 5400.
Therefore, Sum = Rs. 5400.
43. A, B and C start a business each investing Rs. 20000. After 5 months A withdrew Rs. 5000, B
withdrew Rs. 4000 and C invests Rs. 6000 more. At the end of the year, a total profit of Rs. 69,900
was recorded. Find the share of each.
Ans. A’s share = Rs. 20,500
B’s share = Rs. 21200
C’s share = Rs. 28200
Sol: Ratio of the capitals of A, B and C
= (20000*5+ 15000*7) : (20000*5+16000*7): (20000*5+26000*7)
=205000: 212000 : 282000 = 205:212:282
Therefore, A’s share = Rs. ( 69900*205/699) = Rs. 20,500
B’s share = Rs. (69900*212/699) = Rs. 21200,
C’s share = Rs. (69900*282/699) = Rs. 28200.
44. Sanjiv started a business by investing Rs. 36000. After 3 months Rajiv joined him by investing
Rs. 36000. Out an annual profit of Rs. 37100, find the share of each?
Sol: Ratio of their capitals= 36000*12:36000*9 = 4:3
Sanjiv’s share= Rs. ( 37100*4/7) = Rs. 21200.
Rajiv’s share = Rs. ( 37100*3/7) = Rs.15900.
45. If 20 men can build a wall 56m long in 6 days, what length of a similar wall can be built by 35
men in 3 days?
Ans. Length=49m.
Sol: Since the length is to be found out, we compare each item with the length as shown below.
More men, more length built (Direct).
Less days, less length built (Direct).
Men 20:35 :: 56: x
Similarly, days 6:3 :: 56: x.
Therefore, 20*6*x= 35*3*56 or x= 49.
Hence, the required length= 49m.
46.If 9 engines consume 24 metric tonnes of coal, when each is working 8 hours a day; how much
coal will be required for 8 engines, each running 13 hours a day, it being given that 3 engines of the
former type consume as much as 4 engines of latter type.
Ans:26metric tonnes.
Sol: We shall compare each item with the quantity of coal.
Less engines, less coal consumed (direct)
More working hours, more coal consumed (direct)
If 3 engines of former type consume 1 unit, then 1 engine will consume 1/3 unit.
If 4 engines of latter type consume 1 unit, then 1 engine will consume 1/4 unit.
Less rate of consumption, less coal consumed (direct).
Therefore, number of engines 9:8 :: 24:x
Working hours 8:13 :: 24:x
Rate of consumption 1/3:1/4 :: 24:x.
9*8*1/3*x= 8*13*1/4*24 or x= 26.
Therefore, required consumption of coal 26 metric tonnes.
47. A contract is to be completed in 46 days and 117 men were set to work, each working 8 hours a
day. After 33 days 4/7 of the work is completed. How many additional men may be employed so that
the work may be completed in time, each man now working 9 hours a day?
Ans.81
Sol: Remaining work = 1-4/7 =3/7.
Remaining period = (46-33) days =13 days.
Less work, less men (direct)
Less days, more men (indirect).
More hours per day, less men (indirect)
Therefore, work 4/7:3/7 ::117/x
Days 13:33 :: 117/x
Hrs/day 9:8:: 117/x
Therefore, 4/7*13*9*x= 3/7*33*8*117 or x= 198.
Therefore, additional men to be employed =(198-117) =81.
48. A garrison of 3300 men had provisions for 32 days, when given at the rate of 850gms per head.
At the end of 7 days, reinforcement arrives and it was found that the provisions will last 17 days
more, when given at the rate of 825gms per head. What is the strength of the reinforcement?
Ans: 1700
Sol: The problem becomes:
3300 men taking 850gms per head have provisions for (32-7) or 25 days. How many
men taking 825gms each have provisions for 17 days?
Less ration per head, more men (indirect).
Less days, more men (indirect)
Ration 825:850::3300:x
Days 17:25::3300:x
Therefore, 825*17*x= 850*25*3300 or x= 5000.
Therefore, strength of reinforcement = 5000-3300 = 1700.
49. Find the slant height, volume, curved surface area and the whole surface area of a cone of radius
21 cm and height 28 cm.
Sol: Slant Height, l = •(r^2 + h^2) =•(21^2 + 28^2) = •1225 = 35 cm
Volume = 1/3•r^2h = (1/3 * 22/7 * 21 * 21 * 28) cm^3 = 12936 cm^3
Curved surface area = •rl = 22/7 * 21 *35 cm^3 = 2310 cm^2
Total Surface Area = (•rl + •r^2) = (2310 + 22/7 * 21 * 21) cm^2 = 3696 cm^2
50. If the radius of the sphere is increased by 50%, find the increase percent in volume and the
increase percent in the surface area.
Sol: Let the original radius = R. Then, new radius = 150/100 R = 3R/2
Original Volume = 4/3•R^3, New volume = 4/3•(3 R/2)^3 = 9•R^3/2
Original surface area = 4•R^2 , New surface area = 4•(3R/2)^2 = 9•R^2
Increase % in surface area = (5•R^2/4•R^2 * 100)% = 125%
51. If each edge of a cube is increased by 50%, find the percentage increase in its surface area.
Sol: Let the original length of each edge = a
Then, Original surface area = 6a^2
New surface area = 6 * (3a/2)^2 = 27a^2/2
Increase percent in surface area = (15/2a^2 * 1/(6a^2) * 100)% = 125%
52. Find the number of the bricks, each measuring 25 cm by 12.5 cm by 7.5 cm, required to build a
wall 6 m long, 5 m high and 50cm thick, while the mortar occupies 5% of the volume of the wall.
Sol: Volume of the Wall = (600 * 500 * 50) cu. Cm.
Volume of the bricks = 95% of the volume of the wall.
= (95/100 * 600 * 500 * 50) cu. Cm.
Volume of 1 brick = (25 * 25/2 * 75/2) cu. Cm.
Therefore, Number of bricks = (95/100 * (600 * 500 * 50 * 2 * 10)/(25 * 25 * 75))=6080
53. The base of a triangular field is three times its altitude. If the cost of cultivating the field at Rs.
24.68 per hectare be Rs. 333.18, find its base and height.
Sol: Area of the field = Total cost/Rate = (333.18/24.68) hectares =13.5 hectares.
= (13.5*10000) m^2 =135000m^2.
Let altitude = x meters and base = 3x meters.
Then, ½ *3x* x= 135000 or x^2 = 9000 or x= 300.
Therefore, base =900 m & altitude = 300m.
54. Find the area of a rhombus one side of which measures 20cm and one
diagonal
24cm.
Sol: Let, other diagonal = 2x cm,
Since halves of diagonals and one side of rhombus form a right angled
triangle
with side as hypotenuse, we have:
(20)^2 =(12)^2+x^2 or x=Ö(20)^2-(12)^2 =Ö256=16 cm.
Therefore, other diagonal = 32 cm.
55. A tank is fitted with 8 pipes, some of them that fill the tank and others that are waste pipe meant to empty
the tank. Each of the pipes that fill the tank can fill it in 8 hours, while each of those that empty the tank can
empty it in 6 hours. If all the pipes are kept open when the tank is full, it will take exactly 6 hours for the tank
to empty. How many of these are fill pipes?
Sol. Let the number of fill pipes be ‘n'. Therefore, there will be 8-n, waste pipes.
Each of the fill pipes can fill the tank in 8 hours. Therefore, each of the fill pipes will fill 1/8th
of the tank in an hour.
Hence, n fill pipes will fill n/8th of the tank in an hour.
Similarly, each of the waste pipes will drain the full tank in 6 hours. That is, each of the
waste pipes will drain 1/6th of the tank in an hour.
Therefore, (8-n) waste pipes will drain ((8-n)/6)th of the tank in an hour.
Between the fill pipes and the waste pipes, they drain the tank in 6 hours. That is, when all
8 of them are opened, 1/6th of the tank gets drained in an hour.
(Amount of water filled by fill pipes in 1 hour - Amount of water drained by waste pipes 1
hour)
= 1/6th capacity of the tank drained in 1 hour.
56. A pump can be used either to fill or to empty a tank. The capacity of the tank is 3600 m3. The emptying
capacity of the pump is 10 m3/min higher than its filling capacity. What is the emptying capacity of the pump
if the pump needs 12 more minutes to fill the tank than to empty it?
Sol. Let ‘f’ m3/min be the filling capacity of the pump. Therefore, the emptying capacity of the
pump will be = (f + 10 ) m3 / min.
The time taken to fill the tank will be = minutes
And the time taken to empty the tank will be = .
We know that it takes 12 more minutes to fill the tank than to empty it
i.e => 3600 f + 36000 - 3600 f = 12 (f2 + 10 f)
=> 36000 = 12 (f2 + 10 f) => 3000 = f2 + 10 f => f2 + 10 f - 3000 = 0.
Solving for positive value of ‘f’ we get, f = 50.
Therefore, the emptying capacity of the pump = 50 + 10 = 60 m3 / min
57. X alone can do a piece of work in 15 days and Y alone can do it in 10 days. X and Y undertook to do it for
Rs. 720. With the help of Z they finished it in 5 days. How much is paid to Z?
Sol. In one day X can finish 1/15th of the work.
In one day Y can finish 1/10th of the work.
Let us say that in one day Z can finish 1/Zth of the work.
When all the three work together in one day they can finish 1/15 + 1/10 + 1/Z = 1/5th of the
work.
Therefore, 1/Z = 1/30.
Ratio of their efficiencies = 1/15: 1/10: 1/30 = 2: 3: 1.Therefore Z receives 1/6th of the total
money.
According to their efficiencies money is divided as 240: 360: 120.
Hence, the share of Z = Rs. 120.
58. Pipe A usually fills a tank in 2 hours. On account of a leak at the bottom of the tank, it takes pipe A 30
more minutes to fill the tank. How long will the leak take to empty a full tank if pipe A is shut?
Ans:10 hours
Sol. Pipe A fills the tank normally in 2 hours. Therefore, it will fill ½ of the tank in an hour.
Let the leak take x hours to empty a full tank when pipe A is shut. Therefore, the leak will
empty of the tank in an hour.
The net amount of water that gets filled in the tank in an hour when pipe A is open and when
there is a leak = of the tank. — (1)
When there is a leak, the problem states that Pipe A takes two and a half hours to fill the tank. i.e.
hours. Therefore, in an hour, of the tank gets filled. – (2)
Equating (1) and (2), we get => => x = 10 hours.
The problem can also be mentally done as follows.
Pipe A takes 2 hours to fill the tank. Therefore, it fills half the tank in an hour or 50%
of the tank in an hour.
When there is a leak it takes 2 hours 30 minutes for the tank to fill. i.e hours to fill the
tank or or 40% of the tank gets filled.
On account of the leak, (50 - 40)% = 10% of the water gets wasted every hour.
Therefore, the leak will take 10 hours to drain a full tank.
59. How many number of times will the digit ‘7' be written when listing the integers from 1 to 1000?
Sol:7 does not occur in 1000. So we have to count the number of times it appears between 1 and
999. Any number between 1 and 999 can be expressed in the form of xyz where 0 < x, y, z < 9.
1. The numbers in which 7 occurs only once. e.g 7, 17, 78, 217, 743 etc
This means that 7 is one of the digits and the remaining two digits will be any of the other
9 digits (i.e 0 to 9 with the exception of 7)
You have 1*9*9 = 81 such numbers. However, 7 could appear as the first or the second
or the third digit. Therefore, there will be 3*81 = 243 numbers (1-digit, 2-digits and 3-
digits) in which 7 will appear only once.
In each of these numbers, 7 is written once. Therefore, 243 times.
2. The numbers in which 7 will appear twice. e.g 772 or 377 or 747 or 77
In these numbers, one of the digits is not 7 and it can be any of the 9 digits ( 0 to 9 with
the exception of 7).
There will be 9 such numbers. However, this digit which is not 7 can appear in the first
or second or the third place. So there are 3 * 9 = 27 such numbers.
In each of these 27 numbers, the digit 7 is written twice. Therefore, 7 is written 54 times.
3. The number in which 7 appears thrice - 777 - 1 number. 7 is written thrice in it.
Therefore, the total number of times the digit 7 is written between 1 and 999 is 243 + 54
+ 3 = 300
60. There are 5 Rock songs, 6 Carnatic songs and 3 Indi pop songs. How many different albums can be
formed using the above repertoire if the albums should contain at least 1 Rock song and 1 Carnatic song?
Sol: There are 2n ways of choosing ‘n’ objects. For e.g. if n = 3, then the three objects can be
chosen in the following 23 ways - 3C0 ways of choosing none of the three, 3C1 ways of
choosing one out of the three, 3C2 ways of choosing two out of the three and 3C3 ways of
choosing all three.
In the given problem, there are 5 Rock songs. We can choose them in 25 ways. However, as
the problem states that the case where you do not choose a Rock song does not exist (at
least one rock song has to be selected), it can be done in 25 - 1 = 32 - 1 = 31 ways.
Similarly, the 6 Carnatic songs, choosing at least one, can be selected in 26 - 1 = 64 - 1 =
63 ways.
And the 3 Indi pop can be selected in 23 = 8 ways. Here the option of not selecting even
one Indi Pop is allowed.
Therefore, the total number of combinations = 31 * 63 * 8 = 15624
61. A takes 3 min 45 seconds to complete a kilometre. B takes 4 minutes to complete the same 1 km track. If
A and B were to participate in a race of 2 kms, how much start can A give B in terms of distance?
Solution: A can give B a start of 15 seconds in a km race.
B takes 4 minutes to run a km. i.e = 250 m/min = m/sec
Therefore, B will cover a distance of = 62.5 meters in 15 seconds.
The start that A can give B in a km race therefore, is 62.5 meters, the distance that B
run in 15 seconds. Hence in a 2 km race, A can give B a start of 62.5 * 2 = 125 m or
30 seconds.
62. P can give Q a start of 20 seconds in a kilometer race. P can give R a start of 200 meters in the same
kilometer race. And Q can give R a start of 20 seconds in the same kilometer race. How long does P take to
run the kilometer?
Solution:
P can give Q a start of 20 seconds in a kilometer race. So, if Q takes 'x' seconds to run a kilometer, then P will
take x – 20 seconds to run the kilometer.
Q can give R a start of 20 seconds in a kilometer race. So, if R takes 'y' seconds to run a kilometer, then Q will
take y – 20 seconds to run the kilometer.
We know Q takes x seconds to run a kilometer
Therefore, x = y – 20
Therefore, P will take x – 20 = y – 20 – 20 = y – 40 seconds to run a kilometer.
i.e. P can give R a start of 40 seconds in a kilometer race, as R takes y seconds to run a kilometer and P takes
only y – 40 seconds to run the kilometer.
We also know that P can give R a start 200 meters in a km race.
This essentially means that R runs 200 meters in 40 seconds.
Therefore, R will take 200 seconds to run a km.
If R takes 200 seconds to run a km, then P will take 200 – 40 = 160 seconds to run a km.
63. How many squares can be formed using the checkered 1 * 1 squares in a normal chessboard?
Solution:
The number of squares that can be formed using the 1 * 1 checkered squares of a chess board are given by the
relation 12 + 22 + 32 + 42 + ... + 82 = 204
64. A and B enter in to a partnership and A invests Rs. 10,000 in the partnership. At the end of 4
months he withdraws Rs.2000. At the end of another 5 months, he withdraws another Rs.3000. If B
receives Rs.9600 as his share of the total profit of Rs.19,100 for the year, how much did B invest in
the company?
Solution:
The total profit for the year is 19100. Of this B gets Rs.9600. Therefore, A would
get (19100 – 9600) = Rs.9500.
The partners split their profits in the ratio of their investments.
Therefore, the ratio of the investments of A : B = 9500 : 9600 = 95 : 96.
A invested Rs.10000 initially for a period of 4 months. Then, he withdrew Rs.2000.
Hence, his investment has reduced to Rs.8000 (for the next 5 months).
Then he withdraws another Rs.3000. Hence, his investment will stand reduced to Rs.5000
during the last three months.
So, the amount of money that he had invested in the company on a money-month basis
will be = 4 * 10000 + 5 * 8000 + 3 * 5000 = 40000 + 40000 + 15000 = 95000
If A had 95000 money months invested in the company, B would have had 96,000
money months invested in the company (as the ratio of their investments is 95 : 96).
If B had 96,000 money-months invested in the company, he has essentially invested
96000/12 = Rs.8000
65. Four horses are tethered at 4 corners of a square field of side 70 metres so that they just cannot reach one
another. The area left ungrazed by the horses is:
Sol: The length of the rope in which the horses tied should be equal to half of the side of the
square plot so that they just cannot reach one another.
Therefore, the length of the rope is 35m (70/2).
The area covered by each horse should be equal to the area of sector with radius of 70/2 =
35m(length of the rope).
Total area covered by the four horses = 4* area of sector of radius 35 metres = Area of
circle of radius 35m.
Area left ungrazed by the horses = Area of square field - Area covered by four horses.
= 702 - (22/7)*35*35 = 4900 - 3850 = 1050 sq.m.
66. The area of a square field is 24200 sq m. How long will a lady take to cross the field diagonally
at the rate of 6.6 km/hr?
Sol: Let ‘a’ meters be the length of a side of the square field.
Therefore, its area = a2 square meters. --- (1)
We know that the length of the diagonal ‘d’ of a square whose side is ‘a’ meters =
a –-- (2)
From (1) and (2), we can deduce that the square of the diagonal = d2 = 2a2
Or d = meters.
The time taken to cross a length of 220 meters while traveling at 6.6 kmph is
given by (converting
1 km = 1000 meters and 1 hour = 60 minutes).
= 2 minutes
67. For what values of 'm' is y = 0, if y = x2 + (2m + 1)x + m2 - 1? x is a real number.
(1) m -2
(2) m < 0
(3) m = 0
(4) m -1.25
Solution: When x is real, then the discriminant of a quadratic equation (ax2 + bx +
c = 0) 0.
i.e. D = b2 - 4ac 0
In this case,
(2m + 1)2 4(m2 - 1)
4m2 + 4m + 1 4(m2 - 1)
Solving for m, we get m - 1.25
68. A 20 litre mixture of milk and water contains milk and water in the ratio 3 : 2. 10 litres of the mixture is
removed and replaced with pure milk and the operation is repeated once more. At the end of the two removal
and replacement, what is the ratio of milk and water in the resultant mixture?
Solution:
The 20 litre mixture contains milk and water in the ratio of 3 : 2. Therefore, there will be 12 litres of milk in
the mixture and 8 litres of water in the mixture.
Step 1. When 10 litres of the mixture is removed, 6 litres of milk is removed and 4 litres of water is removed.
Therefore, there will be 6 litres of milk and 4 litres of water left in the container. It is then replaced with pure
milk of 10 litres. Now the container will have 16 litres of milk and 4 litres of water.
Step 2. When 10 litres of the new mixture is removed, 8 litres of milk and 2 litres of water is removed. The
container will have 8 litres of milk and 2 litres of water in it. Now 10 litres of pure milk is added. Therefore,
the container will have 18 litres of milk and 2 litres of water in it at the end of the second step.
Therefore, the ratio of milk and water is 18 : 2 or 9 : 1.
69. A merchant mixes three varieties of rice costing Rs.20/kg, Rs.24/kg and Rs.30/kg and sells the mixture at
a profit of 20% at Rs.30 / kg. How many kgs of the second variety will be in the mixture if 2 kgs of the third
variety is there in the mixture?
Solution:
If the selling price of mixture is Rs.30/kg and the merchant makes a profit of 20%, then the cost price of the
mixture = = Rs.25/kg.
We need to find out the ratio in which the three varieties are mixed to obtain a mixture costing Rs.25 /kg.
Let variety A cost Rs.20/kg, variety B cost Rs.24 / kg and variety C cost Rs.30/kg. The mean desired price
falls between B and C.
Step 1: Find out the ratio QA : QC using alligation rule.
Step 2: Find out the ratio QB : QC using alligation rule.
Step 3: QC is found by adding the value of QC in step 1 and step 2 = 1 + 1 = 2
Therefore, the required ratio = 1 : 5 : 2
If there are 2 kgs of the third variety in the mixture, then there will be 5 kgs of the second variety in the
mixture.
70.Rs.432 is divided amongst three workers A, B and C such that 8 times A’s share is equal to 12 times B’s
share which is equal to 6 times C’s share. How much did A get?
Solution:
8 times A’s share = 12 times B’s share = 6 times C’s share.
Note that this is not the same as the ratio of their wages being 8 : 12 : 6
In this case, find out the L.C.M of 8, 12 and 6 and divide the L.C.M by each of the above numbers to get the
ratio of their respective shares.
The L.C.M of 8, 12 and 6 is 24.
Therefore, the ratio A:B:C :: => A : B : C :: 3 : 2 : 4
The sum of the total wages = 3x + 2x + 4x = 432 => 9x = 432 or x = 48.
Hence A gets 3 * 48 = Rs. 144.
71. A zookeeper counted the heads of the animals in a zoo and found it to be 80. When he counted the legs of
the animals he found it to be 260. If the zoo had either pigeons or horses, how many horses were there in the
zoo?
Solution:
Let the number of horses = x
Then the number of pigeons = 80 – x.
Each pigeon has 2 legs and each horse has 4 legs.
Therefore, total number of legs = 4x + 2(80-x) = 260
=>4x + 160 – 2x = 260
=>2x = 100
=>x = 50.
72. A group of workers can do a piece of work in 24 days. However as 7 of them were absent it took 30 days
to complete the work. How many people actually worked on the job to complete it?
Solution:
Let the original number of workers in the group be 'x'
Therefore, actual number of workers = x-7.
We know that the number of manhours required to do the job is the same in both the cases.
Therefore, x (24) = (x-7).30
24x = 30x - 210
6x = 210
x = 35.
Therfore, the actual number of workers who worked to complete the job = x - 7 = 35 -7 = 28.
73. How many litres of water should be added to a 30 litre mixture of milk and water containing milk and
water in the ratio of 7 : 3 such that the resultant mixture has 40% water in it?
Solution:
30 litres of the mixture has milk and water in the ratio 7 : 3. i.e. the solution has 21 litres of milk and 9 litres
of water.
When you add more water, the amount of milk in the mixture remains constant at 21 litres. In the first case,
before addition of further water, 21 litres of milk accounts for 70% by volume. After water is added, the new
mixture contains 60% milk and 40% water.
Therefore, the 21 litres of milk accounts for 60% by volume.
Hence, 100% volume = = 35 litres.
We started with 30 litres and ended up with 35 litres. Therefore, 5 litres of water was added.
74. The ratio of marks obtained by vinod and Basu is 6:5. If the combined average of their percentage is 68.75
and their sum of the marks is 275, find the total marks for which exam was conducted.
Solution:
Let Vinod marks be 6x and Basu's is 5x. Therefore, the sum of the marks = 6x + 5x = 11x.
But the sum of the marks is given as 275 = 11x. We get x = 25 therefore, vinod marks is 6x = 150 and Basu
marks = 5x = 125.
Therefore, the combined average of their marks = (150 + 125) / 2 = 137.5.
If the total mark of the exam is 100 then their combined average of their percentage is 68.75
Therefore, if their combined average of their percentage is 137.5 then the total marks would be (137.5 / 68.75)
*100 = 200.
75. A spherical ball of radius 'r' placed on the ground subtends an angle of 600 at point A of the ground. What
is the distance between the center of the ball and the point A?
Solution:
In an equilateral triangle all three sides are of the same length and let this be 'a' units.
From the diagram it is clear that OA is the angle bisector of angle LAM.
Therefore, angle OAL = 30In the right triangle OAL, sin 30 =
We know that OL is the radius of the sphere = r
Therefore,
Or OA = 2r
76. If the cost price of 20 articles is equal to the selling price of 16 articles, What is the percentage of profit or
loss that the merchant makes?
Solution:
Let Cost price of 1 article be Re.1.
Therefore, Cost price of 20 articles = Rs. 20.
Selling price of 16 articles = Rs. 20
Therefore, Selling price of 20 articles = (20/16) * 20 = 25
Profit = Selling price - Cost price
= 25 - 20 = 5
Percentage of profit = Profit / Cost price * 100.
= 5 / 20 * 100 = 25% Profit
77. A candidate who gets 20% marks fails by 10 marks but another candidate who gets 42% marks gets 12%
more than the passing marks. Find the maximum marks.
Solution:
Let the maximum marks be x.
From the given statement pass percentage is 42% - 12% = 30%
By hypothesis, 30% of x – 20% of x = 10 (marks)
i.e., 10% of x = 10
Therefore, x = 100 marks.
78. Train A traveling at 60 km/hr leaves Mumbai for Delhi at 6 P.M. Train B traveling at 90 km/hr also leaves
Mumbai for Delhi at 9 P.M. Train C leaves Delhi for Mumbai at 9 P.M. If all three trains meet at the same
time between Mumbai and Delhi, what is the speed of Train C if the distance between Delhi and Mumbai is
1260 kms?
Solution:
All three trains meet at the same time between Delhi and Mumbai. Which means Train A and Train B are at
the same point at that time. This will happen when Train B is overtaking Train A.
Train A starts 3 hours before Train B. Therefore, by the time Train B leaves Mumbai, Train A has covered 3 *
60 = 180 kms.
The relative speed between Train A and Train B = 90 - 60 = 30 kmph. Therefore, Train B will overtake Train
A in 180/30= 6 hours from the time Train B leaves Mumbai. That is at 3 A.M, Train B will overtake Train A.
The point between Mumbai and Delhi at which Train B overtakes Train A will be 6*90=540 kms from
Mumbai.
Train C will also be at that point at 3 A.M while Train B is overtaking Train A. And Train C would have
travelled 1260-540 = 720 kms in these 6 hours. Therefore, the speed of Train C = 720/6= 120 km/hr.
79. In an election contested by two parties, Party D secured 12% of the total votes more than Party R. If party
R got 132,000 votes, by how many votes did it lose the election?
Solution:
Let the percentage of the total votes secured by Party D be x%
Then the percentage of total votes secured by Party R = (x – 12)%
As there are only two parties contesting in the election, the sum total of the votes secured by the two parties
should total up to 100%
i.e., x + x – 12 = 100
2x – 12 = 100
or 2x = 112 or x = 56%.
If Party D got 56% of the votes, then Party got (56 – 12) = 44% of the total votes.
44% of the total votes = 132,000 i.e., 44/100xT= 132,000
ð T = 132,000x100/44= 300,000 votes.
The margin by which Party R lost the election = 12% of the total votes
= 12% of 300,000 = 36,000.
80. Two trains A and B start simultaneously from stations X and Y towards each other respectively. After
meeting at a point between X and Y, train A reaches station Y in 9 hours and train B reaches station X in 4
hours from the time they have met each other. If the speed of train A is 36 km/hr, what is the speed of train B?
Solution:
The ratio of the speed of the two trains A and B is given by
, where b is the time taken by train B to reach its destination after meeting train A and
a is the time taken by train A to reach its destination after meeting train B.
In this case,
ð Speed of train B = * Speed of train A = * 36 = 54 km/hr
81. When processing flower-nectar into honeybees' extract, a considerable amount of water gets reduced.
How much flower-nectar must be processed to yield 1kg of honey, if nectar contains 50% water, and the
honey obtained from this nectar contains 15% water?
Solution:
Flower-nectar contains 50% of non-water part.
In honey this non-water part constitutes 85% (100-15).
Therefore 0.5 X Amount of flower-nectar = 0.85 X Amount of honey = 0.85 X 1 kg
Therefore amount of flower-nectar needed = (0.85/0.5) * 1kg = 1.7 kg.
82. Two boys begin together to write out a booklet containing 535 lines. The first boy starts with the first line,
writing at the rate of 100 lines an hour; and the second starts with the last line then writes line 534 and so on,
backward proceeding at the rate of 50 lines an hour. At what line will they meet?
Solution:
Writing ratio = 100:50= 2:1
Since equal quantities are taken,
Therefore in a given time, first boy will be writing the line number
2/xX535 or 356 2/3 or 357th line
Hence, both of them shall meet on 357th line
83. If the price of petrol increases by 25%, by how much must a user cut down his consumption so that his
expenditure on petrol remains constant?
Solution:
Let the price of petrol be Rs.100 per litre. Let the user use 1 litre of petrol. Therefore, his expense on petrol =
100 * 1 = Rs.100
Now, the price of petrol increases by 25%. Therefore, the new price of petrol = Rs.125.
As he has to maintain his expenditure on petrol constant, he will be spending only Rs.100 on petrol.
Let ‘x’ be the number of litres of petrol he will use at the new price.
Therefore, 125*x = 100 => x = 100/125 = 4/5=0.8 litres.
He has cut down his petrol consumption by 0.2 litres = 0.2/1*100= 20% reduction.
There is a short cut for solving this problem.
If the price of petrol has increased by 25%, it has gone up 1/4th of its earlier price.
Therefore, the % of reduction in petrol that will maintain the amount of money spent on petrol constant = 1/
(4+1)= 1/5= 20%
84. A train traveling at 72 kmph crosses a platform in 30 seconds and a man standing on the platform in 18
seconds. What is the length of the platform in meters?
Solution:
When the train crosses a man standing on a platform, the distance covered by the train is equal to the length of
the train.
However, when the same train crosses a platform, the distance covered by the train is equal to the length of
the train plus the length of the platform.
The extra time that the train takes when crossing the platform is on account of the extra distance that it has to
cover = length of the platform.
Therefore, length of the platform = speed of train * extra time taken to cross the platform
Length of platform = 72 kmph * 12 seconds
converting 72 kmph into m/sec, we get 72 kmph = 5/18*72= 20 m/sec
Therefore, length of the platform = 20 * 12 = 240 meters.
85. A man can row 50 km upstream and 72 km downstream in 9 hours. He can also row 70 km upstream and
90 km downstream in 12 hours. Find the rate of current.
Solution:
Let x and y be the upstream and downstream speed respectively.
Hence 50/x + 72/y = 9 and 70/x + 90/y = 12
Solving for x and y we get x = 10 km/hr and y = 18 km/hr
We know that Speed of the stream = 1/2 * (downstream speed - upstream speed) = 1/2 (18 – 10) = 4 km/hr.
86. By walking at 3/4th of his usual speed, a man reaches office 20 minutes later than usual. What is his usual
time?
Solution:
3/4 of a man's usual speed means, he takes 4/3 of his usual time to cover the same distance, i.e. he takes 4/3 –
1 = 1/3 time extra.
1/3 time is 20 minutes (given)
Usual time = 20 * 3 = 60 minutes.
87. Yana and Gupta leave points x and y towards y and x respectively simultaneously and travel in the same
route. After meeting each other on the way, Yana takes 4 hours to reach her destination, while Gupta takes 9
hours to reach his destination. If the speed of Yana is 48 km/hr, what is the speed of Gupta?
Solution:
Yana and Gupta travel for the same amount of time till the time they meet between x and y.
So, the distance covered by them will be the same as the ratio of their speeds. Let the time that they have
taken to meet each other be x hours from the time they have started.
Therefore, the cover the entire distance, Yana would take x + 4 hours and Gupta will take x + 9 hours.
Ratio of time taken Yana : Gupta :: x + 4 :: x + 9
=>Ratio of speeds of Yana : Gupta :: x + 9 :: x + 4 or 1 : (x+4)/(x+9)
By the time Yana and Gupta meet, Yana would have traveled 48X kms. After meeting, this is the distance that
Gupta takes 9 hours to cover.
Hence, Gupta's speed = 48x/9 km/hr.
=> But we know that the ratio of Yana's and Gupta's speeds are 1 : (x+4)/(x+9)
=> Therefore, 48 : 48x/9:: 1 : x+4/x+9
Or x/9= x+4/x+9
=> x2 + 9x = 9x + 36
=> x2 = 36 or x = 6 hours.
Hence, speed of Gupta = 48x/9=48*6/9= 32 kmph = 20mph
88. The difference between the compound interest and the simple interest on a certain sum at 12% p.a. for two
years is Rs.90. What will be the value of the amount at the end of 3 years?
Solution:
The difference in the simple interest and compound interest for two years is on account of the interest paid on
the first year's interest, when interest is reckoned using compound interest, interest being compounded
annually.
Hence 12% of simple interest = 90 => simple interest = 90/0.12=750.
As the simple interest for a year = 750 @ 12% p.a., the principal = 750/0.12= Rs.6250.
If the principal is 6250, then the amount outstanding at the end of 3 years = 6250 + 3(simple interest on 6250)
+ 3 (interest on simple interest) + 1 (interest on interest on interest) = 6250 + 3(750) + 3(90) + 1(10.80) =
8780.80.
89. How long will it take for a sum of money to grow from Rs.1250 to Rs.10,000, if it is invested at 12.5% p.a
simple interest?
Solution:
Simple interest is given by the formula SI = (pnr/100), where p is the principal, n is the number of years for
which it is invested, r is the rate of interest per annum
In this case, Rs. 1250 has become Rs.10,000.
Therefore, the interest earned = 10,000 – 1250 = 8750.
8750 = [(1250*n*12.5)/100]
=> n = 700 / 12.5 = 56 years.
90. If the wheel of a bicycle makes 560 revolutions in travelling 1.1 km, what is its radius?
Solution:
The distance covered by the wheel in 560 revolutions = 1100 m . Hence, the distance covered per revolution =
100/560=55/28metres.
The distance covered in one revolution = circumference of the wheel.
Circumference = 2 pi r=> 2x22/7 xr = 31.25 cm.
91. The time in a clock is 20 minute past 2. Find the angle between the hands of the clock.
Solution:
Time is 2:20. Position of the hands: Hour hand at 2 (nearly).
Minute hand at 4
Angle between 2 and 4 is 60 degrees [(360/12) * (4-2)]
Angle made by the hour hand in 20 minutes is 10 degrees, since it turns through ½ degrees in a minute.
Therefore, angle between the hands is 60 degrees - 10 degrees = 50 degrees
92. A man buys an article for Rs. 27.50 and sells it for Rs. 28.60. Find his gain percent.
Solution:
C.P. = Rs.27.50, S.P. = Rs. 28.60.
Therefore Gain = Rs. (28.60 – 27.50) = Rs.1.10.
Therefore Gain % = (1.10*100/27.50) % = 4%.
93. Find S.P., when:
(i) C.P. = Rs. 56.25, gain = 20%.
(ii) C.P. = Rs. 80.40, loss = 15%.
Solution:
(i) S.P. = 120% of Rs. 56.25 = Rs. (120*56.25/100) = Rs. 67.50.
(ii) S.P. = 85% of Rs. 80.40 = Rs. (85*80.40/100) = Rs. 68.34.
94. A scooterist covers a certain distance at 36 kmph. How many meters does he cover in 2min?
Solution:
Speed = 36 kmph = 36 * 5/18 = 10mps
Therefore, Distance covered in 2 min = (10 * 2 * 60)m = 1200m
95. A gentleman buys every year Bank's cash certificates of value exceeding the last year's purchase by Rs.
300. After 20 years, he finds that the total value of the certificates purchased by him is Rs. 83,000. Find the
value of the certificates purchased by him in the 13th year.
Solution:
Let the value of the certificates purchased in the first year be Rs. a.
The difference between the value of the certificates is Rs. 300 (d = 300).
Since, it follows Arithmetic progression the total value of the certificates after 20 years is given by
Sn = n/2 [2a + (n - 1) d] = 20/2[2a + 19(300)] = 83,000.
By simplifying we get 2a + 5700 = 8300.
Therefore, a = Rs. 1300.
The value of the certificates purchased by him in nth year = a + (n - 1) d.
Therefore, the value of the certificates purchased by him in 13th year = 1300 + (13 - 1) 300 = Rs. 4900.
96. How often between 11 O'clock and 12 O'clock are the hands of the clock together at an integral number
value?
Solution:
At 11 O'clock, the hour hand is 5 spaces apart from the minute hand.
During the next 60 minutes, i.e. between 11' O clock and 12' O clock the hour hand will move five spaces
[integral values as denoted by the 56 minute, 57 minute, 58 minute, 59 minute and 60 minute positions].
For each of these 5 positions, the minute hand will be at the 12th minute, 24th minute, 36th minute, 48th
minute and 60th minute positions.
Hence the difference between the positions of the hour hand and the minute hand will have an integral number
of minutes between them.
i.e. 5 positions.
97. At how many points between 10 O'clock and 11 O'clock are the minute hand and hour hand of a clock at
an angle of 30 degrees to each other?
Solution:
Between 10 and 11, the minute hand and hour hand are at an angle of 30o to each at (12/11)x45minutes past
10 = 49 1/11minutes past 10. The next time they will be at angle of 30o to each other will be at 11.
98. A clock loses 1% time during the first week and then gains 2% time during the next one week. If the clock
was set right at 12 noon on a Sunday, what will be the time that the clock will show exactly 14 days from the
time it was set right?
Solution:
The clock loses 1% time during the first week.
In a day there are 24 hours and in a week there are 7 days. Therefore, there are 7 * 24 = 168 hours in a week.
If the clock loses 1% time during the first week, then it will show a time which is 1% of 168 hours less than
12 Noon at the end of the first week = 1.68 hours less.
Subsequently, the clock gains 2% during the next week. The second week has 168 hours and the clock gains
2% time = 2% of 168 hours = 3.36 hours more than the actual time.
As it lost 1.68 hours during the first week and then gained 3.36 hours during the next week, the net result will
be a -1.68 + 3.36 = 1.68 hour net gain in time.
So the clock will show a time which is 1.68 hours more than 12 Noon two weeks from the time it was set
right.
1.68 hours = 1 hour and 40.8 minutes = 1 hour + 40 minutes + 48 seconds.
i.e. 1 : 40 : 48 P.M.
99. What is the angle between the minute hand and the hour hand when the time is 1540 hours?
Solution:
The total angle made by the minute hand during an hour is 360o. If it takes 360o for an hour, it will take
(40/60)*360= 240o. The angle between the hour hand the minute hand will therefore, be somewhere between
240 - 90 = 150o, as the hour hand is between 3 and 4.
The angle made by the hour hand when it moves from say 3 to 4 will be 30o. That is the hour hand makes 30o
during the course of an hour.
The hour hand will therefore, move (40/60)*30= 20o.
Therefore, the net angle between the hour hand and the minute hand will be 150 - 20 = 130o.
100. Given that on 27th February 2003 is Thursday. What was the day on 27th February 1603?
Solution:
After every 400 years, the same day occurs.
Thus, if 27th February 2003 is Thursday, before 400 years i.e., on 27th February 1603 has to be Thursday.